As business leaders, it is easy to get caught up in our day-to-day operations while overlooking the bigger technology picture. However, relying on outdated hardware and software can lead to unforeseen expenses that affect profits, productivity, and reputation.
Effective management of technology lifecycles is important to minimise risks and support growth. Regularly evaluating your existing IT infrastructure in line with your IT investment and broader strategy is essential.
Additionally, understanding the need to craft a persuasive business rationale for technology investment is important for future prosperity. Effectively communicating the advantages, making precise forecasts on returns, and rallying support for essential upgrades to your technological framework are key steps toward unincumbered growth.
Aging Tech Risks: The Dangers of Falling Behind
Using outdated systems puts your business at a disadvantage compared to competitors and exposes it to risks. The primary dangers associated with sticking to aging IT infrastructure range from heightened vulnerability to cyber-attacks and system failures, reduced efficiency, and diminished customer satisfaction.
Recognising these obstacles is the first initial step toward driving your business forward with effective solutions. Let us clarify these inefficiencies in more detail:
- Decreased Productivity: Older devices and software often run slower and are more prone to crashes, resulting in frustrating delays and lost productivity for your employees.
- Security Vulnerabilities: Aging technology may no longer receive crucial security updates, leaving your systems vulnerable to cyber threats, data breaches, and potential legal and financial consequences.
- Limited Functionality: Outdated software may not be compatible with updated file formats or integrate with current systems, hindering collaboration and limiting your team’s ability to leverage the latest tools and features.
- Higher Maintenance Costs: As hardware and software age, they require frequent repairs and maintenance, leading to increased IT support costs and potential downtime.
A Real-World Example
During a recent meeting with our client, an early childhood provider, we observed that many of its devices were aging and out of warranty. Some of these devices date back to 2016 models, which means they no longer meet the minimum requirements for upgrading to the next Windows operating system. The technology has also become unfit for the school’s current working strategy.
This situation highlights the importance of proactively managing technology lifecycles to prevent potential disruptions and increased costs. The current plan is to shift to a more agile tech format that is less resource-intensive for the school’s IT needs.
Technology Lifecycle Management Essentials
Effective technology lifecycle management is crucial for maintaining a competitive edge and achieving operational efficiency. By managing the lifecycle of your technology assets—from procurement to retirement—you ensure that your business remains agile, secure, and ahead of the curve.
Below are IT strategies for lifecycle management that not only mitigate risks but also optimise your technology investments for sustained growth and innovation.
- Plan for Regular Upgrades: Develop a technology roadmap that includes regular hardware and software upgrades to ensure your systems remain up-to-date, secure, and capable of supporting your business needs.
- Allocate Funds for Upgrades: Include technology upgrades in your annual budget to avoid unexpected expenses and ensure you have the necessary funds to replace or improve your IT infrastructure before it becomes a critical issue.
- Conduct Regular IT Infrastructure Assessments: Regularly review your existing technology to identify devices and software approaching end-of-life, evaluate their performance and security, and prioritise areas for improvement.
Executing tangible lifecycle strategies will allow businesses to significantly mitigate the adverse effects of aging technology. This focused approach reduces security risks and operational inefficiencies, fostering a culture of continuous improvement and innovation.
Related: The Importance of having a Technology Roadmap for Your Business
Building a Business Case for Technology Investment
Crafting a compelling business case for technology investment is vital to ensure your company’s ongoing success. It is important to clearly articulate the benefits, accurately predict the returns, and garner support for the necessary updates to your IT infrastructure. Below are key factors and actions to advocate for technology upgrades to senior management:
- Highlight Immediate and Long-Term Benefits: Begin by outlining how the investment will address current pain points, such as reducing operational costs or enhancing security. Additionally, emphasise the longer-term advantages, including improved efficiency, scalability, and competitiveness.
- Provide a Detailed Cost-Benefit Analysis: Demonstrating the financial impact is crucial. Offer a detailed analysis that compares the costs of upgrading versus the costs of maintaining current systems, including the potential for increased revenue or cost savings.
- Showcase Success Stories: Providing examples of successful technology investments, either from within your organisation or from industry peers, can help build confidence in the proposed upgrades. Highlight the challenges they faced, the solutions they implemented, and the benefits they reaped.
- Highlight Risks of Inaction: Clearly articulate the risks and potential costs of not investing in new technology, such as system failures, security breaches, and falling behind competitors.
By focusing on these areas, you will be better positioned to secure the necessary backing required for your technology investments. This, in turn, will enable you to make well-informed decisions that contribute to future growth and resilience.
Prioritise your IT Infrastructure
Neglecting your business’s technology infrastructure can have far-reaching consequences that impact your bottom line.
By recognising the risks of aging hardware and software, prioritising lifecycle management, and building a strong business case for important upgrades, you can proactively address potential issues and ensure your technology supports your business’s success.
Do not wait until outdated systems cause major disruptions – act today to assess your IT infrastructure and invest in the technology your business needs to thrive.
Technology plays a crucial role in the success of any organisation. However, many businesses struggle with the implementation of an effective and ongoing technology strategy. The solution? A comprehensive technology roadmap!
But why is a roadmap so vital? A technology roadmap is the link between your IT strategy and the successful execution of that strategy. It’s where the rubber hits the road with practical, prioritised actions to bring your strategy to life. A technology roadmap is essential for businesses aiming to thrive and grow. By remaining competitive, fostering productivity, and ensuring robust support for future endeavours, a well-crafted roadmap paves the way for success.
Why You Need a Technology Roadmap
It’s important to understand the tangible benefits a technology roadmap brings to an organisation. A well-crafted roadmap not only guides a company through its current technology landscape but also steers it towards future growth and innovation. In the following section, we’ll explore the significant advantages of developing and maintaining a technology roadmap for your business.
- Alignment with Business Objectives: A technology roadmap ensures that your IT investments and initiatives are proactively aligned with your overall business strategy and goals.
- Improved Budgeting and Resource Allocation: By planning ahead, you can allocate your budget and resources more effectively, avoiding unexpected costs and ensuring that you have the necessary funds for critical projects.
- Enhanced Efficiency and Productivity: A well-planned technology roadmap helps you streamline your processes, automate tasks, and improve collaboration among team members, ultimately boosting efficiency and productivity.
- Cybersecurity and Risk Management: In today’s technology landscape early detection of cyber threats is crucial. A data breach incident risks suspending your daily business operations and can cost your business large amounts of money. A technology roadmap allows you to identify potential risks and vulnerabilities in your IT infrastructure and implement measures to mitigate them, safeguarding your business against potential cyber threats.
- Competitive Advantage: By staying up to date with the latest technology trends and implementing them strategically, you can gain a competitive edge in your industry. An example of this is how AI technology can transform your business productivity overnight.
Key Components of an Effective Technology Roadmap
A technology roadmap is a strategic plan that outlines how technology will be applied to support and enhance your business strategy over a specific period. It serves as a planning tool to communicate a clear IT strategy throughout your organisation. Some crucial components in the development of your roadmap include:
- Assessment of Current Technology: Start by evaluating your current technology estate, identifying any gaps or areas for improvement. This assessment should outline the following:
- Evaluation of Technologies in Use: Scrutinise the effectiveness and efficiency of each technology component in fulfilling its designated role within the business ecosystem.
- Technology Outlook: Developing a nuanced understanding of your current technology landscape is pivotal for identifying potential gaps, areas for enhancement, and opportunities for innovation.
- Alignment with Business Goals: The starting point for any technology roadmap must be the business’s goals and objectives. Whether it’s improving customer experience, increasing operational efficiency, or expanding into new markets, the roadmap should clearly illustrate how technology will help achieve these goals.
- Prioritisation of Projects: Firstly, prioritise your technology initiatives based on their impact on your business, urgency, and feasibility.
- Timeline and Milestones: An effective technology roadmap will provide a timeline that outlines when each technology initiative will begin and end. This helps businesses allocate resources efficiently and ensures that technology initiatives are aligned with business objectives in a timely manner.
- Budget and Resource Allocation: Implementing new technology can be resource intensive. A technology roadmap should include a detailed budget that covers the costs associated with each initiative, including hardware and software expenses, training costs, and additional staffing needs. It should also outline how resources will be allocated to ensure the successful execution of each technology initiative.
- Ongoing Monitoring and Adjustment: Regularly monitor your progress and make adjustments as needed to ensure that you stay on track and adapt to any changes in your business environment.
By incorporating these key components into your technology roadmap, your business can ensure that its technology investments are strategic, targeted, and aligned with long-term business goals.
Tips for Working with Trusted IT Partners To Develop Your Roadmap
When developing a technology roadmap in collaboration with IT partners, it’s essential to ensure a smooth and effective planning process. Here are some tips for working alongside your IT partners to craft an effective technology roadmap:
- Choose the Right Partner: Select an IT provider that has experience working with businesses like yours at a strategic level. It’s important for them to understand your industry’s unique challenges and opportunities. At the very least they should be willing to learn about your industry.
- Communicate Your Business Goals Clearly: Start by clearly outlining your business goals and objectives to your IT partners. This ensures that the technology solutions proposed are in line with your business’s strategic direction.
- Engage in Collaborative Planning: Involve your IT partners in the planning process from the outset. Their expertise can provide valuable insights into the latest technology trends that could benefit your business and help identify potential challenges early on.
- Set Realistic Expectations: Technology projects often encounter unforeseen challenges. Work with your IT partners to set realistic timelines and budget expectations for each initiative within the roadmap.
- Foster Open Communication: Maintain open lines of communication with your IT partner, regularly sharing updates and feedback to ensure that everyone is on the same page. Your IT partner should be willing to listen to your pain points and suggest helpful pathways to improve your IT strategy and productivity.
- Prioritise Flexibility: Technology and business needs change rapidly. Ensure your technology roadmap has the flexibility to adapt to new trends and business objectives as they arise.
- Be Open to Recommendations: Your IT partner brings valuable expertise and insights to the table. Be open to their recommendations and advice when making decisions about your technology roadmap.
- Focus on Security and Compliance: Ensure that your IT partners understand the importance of security and compliance within your industry. Incorporating these considerations from the start can prevent costly adjustments later on.
- Review and Update Regularly: Technology roadmaps are not static documents. Regular reviews with your IT partners will help you adjust your roadmap as needed, ensuring it continues to align with your business goals and the technological landscape.
By following these tips, businesses can effectively collaborate with IT partners to develop an effective strategy that not only meets their current technology needs but also positions them for future growth and innovation!

How Your Business Can Benefit From a Strategic Technology Roadmap
Having a well-defined technology roadmap is essential for any business looking to stay competitive and achieve its goals. By aligning your technology initiatives with your business objectives, prioritising projects, and working closely with a trusted IT partner, you can develop a roadmap that supports long-term success. Additionally, it will also optimise your:
- budget and resource allocation
- enhance operational efficiency and productivity
- cybersecurity & risk management
Remember to regularly review and update your plan to ensure that you stay on track and adapt to any changes in your industry or business environment. Lastly, effective collaboration with IT partners during the development of this roadmap ensures that technology initiatives remain relevant and adaptable.
These initiatives should meet current needs while also being flexible enough to accommodate future shifts. Ultimately, a technology roadmap serves as an invaluable tool for businesses seeking to fully harness technology’s potential to drive growth, innovation, and long-term success! Contact our friendly team today to discover how we can help you devise and implement a robust roadmap for your business.
With new and evolving cybersecurity threats emerging almost daily, the risk to businesses is greater than ever. A 2023 study by IBM reports that the average cost of a data breach in Australia is now $4.3 million. While this figure is less than the global average of $4.45 million, the escalation of cybersecurity threats shows no sign of slowing anytime soon.
So, the critical question is, how do you keep your organisation safe in such a hostile cyber environment? The best place to start is by educating yourself on the nature of cybersecurity risks and the options available to help mitigate them.
In this post, we discuss the top five cybersecurity threats to be aware of in 2024. These are the most common threats that we see in our work helping clients mitigate these risks and respond to incidents.
1. Increased Impact from Malicious AI Tools
Artificial Intelligence (AI) poses a significant threat, not just as a tool for innovation but also as a potential weapon in the hands of cybercriminals.
AI can be exploited by cybercriminals to conduct more sophisticated attacks with increased precision and frequency. These AI-driven attacks can bypass traditional cybersecurity measures, making detection and defence more challenging for organisations.
Strategies to Combat Malicious AI Tools:
Developing strategies to counteract malevolent AI tools is important for safeguarding your organisation against complex threats. By remaining proactive and employing security practices, you can diminish the risks and consequences of AI-powered cyber-attacks. Here are helpful strategies to combat these threats:
- Continuous Monitoring: Implement AI-driven security tools that monitor network activity to detect and respond to anomalies. These tools can detect anomalies and respond promptly to any suspicious behaviour.
- Advanced Threat Intelligence: Leverage platforms that use AI to predict and identify potential threats before they can cause harm.
- Regular Security Audits: Conduct frequent cybersecurity risk assessments to identify vulnerabilities and ensure all security protocols are up to date.
Organisations can enhance their protection against the increasing threat of malicious AI by staying proactive and utilising AI defence tools.
2. Phishing
Phishing is one of the most common forms of attack whereby fake emails are sent purporting to be from sources familiar to the target, such as the Commonwealth Bank, Australia Post or Microsoft. The goal of phishing is to trick individuals into granting access to secure systems by either handing over password details or allowing the installation of malware onto their computer. Once the attacker has gained access to company systems, they may explore and plan their next steps undetected.
Protecting Against Phishing
- Multi-factor Authentication (MFA): Even if an attacker obtains password details, MFA adds a layer of security. Most modern applications support MFA, though it may not be enabled by default.
- Email Filtering: Effective email filtering can stop many phishing emails before they reach employee inboxes. Advanced filtering is available for major platforms like Microsoft Office 365.
- User Education: Employee awareness is critical. Educating your workforce on recognising and avoiding phishing attacks is an effective risk mitigation strategy.
3. Business Email Compromise
Business email compromise is a strategy used by attackers to defraud a target company, employed once they have gained access to secure systems via other means. With access to company systems, they will gather information regarding financial processes, payment systems and client relationships. They will monitor email communications to learn who in the organisation has financial authority and the language and methods that they use to communicate.
Once they have the information that they need, attackers will then seek to deceive employees, clients and business partners into making payments to their bank accounts rather than genuine ones. These fraudulent requests for funds can be difficult to identify and lost funds can be challenging to trace and recover. The potential for direct financial loss through business email compromise is significant.
Protecting Against Business Email Compromise
- Multi-factor Authentication (MFA): MFA effectively defends against many user account attacks.
- User Education: Employees involved in financial transactions must be vigilant and take all necessary precautions.
- Verification Processes: Implement secondary verification (e.g., phone calls) for all financial transactions and change of detail requests.
4. Social Engineering
Cybercriminals will often seek to gain the trust of their targets in order to elicit the information that they need to breach secure systems. Any form of social interaction with the malicious intent of gaining access to secure systems can be considered social engineering. A common approach is to create fictitious personas on social media which are then used to establish fake relationships with potential victims and trick them into allowing access to company systems.
Protecting Against Social Engineering
- User Education: Training employees to identify and respond to social engineering threats is essential.
- Endpoint Protection: Use advanced endpoint protection software to detect and block malicious software.
- Multi-factor Authentication (MFA): MFA provides robust defence against user account breaches, even if passwords are compromised.
5. Ransomware
Ransomware is a particular form of malicious software (aka malware) that, once active within a computer system, will encrypt critical data rendering it inaccessible until a ransom is paid. Unfortunately for some business owners, even when a ransom is paid, access to the data is not always restored. Ransomware is responsible for some of the largest and highest profile security incidents in recent times. A ransomware attack can be devastating to any organisation, grinding operations to a halt.
Protecting against Ransomware
All forms of malware including ransomware can be mitigated with strategies such as:
- Endpoint protection: All computer systems must be protected with advanced endpoint protection software.
- System updates: Computer systems without up-to-date software and operating systems are a common weakness that attackers can exploit.
- Isolated backups: Not only should backups be monitoring and tested regularly, but a copy should be stored separately and unattached to the main systems to protect attackers from being able to compromise backups.
- User education: Human error is common factor in many malware infections. Training employees to recognise a potential malware infection and respond accordingly is critical.
6. Supply Chain Attack
A supply chain attack is a form of cyber-attack where malicious actors target an organisation indirectly through less secure partners in their supply chain, most commonly software vendors. The attackers aim to compromise a particular software application which, once deployed in the target organisation’s network, allows unauthorised access to company systems. Such attacks can have widespread repercussions, as compromising one link in the supply chain can potentially grant access to multiple interconnected organisations.
Although not strictly a supply chain attack, it’s important to highlight the necessity for supply chain cyber-resilience. An attack on your supply chain can be just as disruptive as an attack through your supply chain. Disruptions to key suppliers can cause significant operational downtime and extend vulnerabilities within your organisation.
Protecting against Supply Chain Attack
- Risk management: Include Supply Chain in risk management plans, including disaster recovery and cybersecurity incidents.
- Least trust security: Limit supplier access to the minimum required.
- Vendor security requirements: Incorporate clear vendor security requirements into supply agreements.
Watch our free on-demand webinar now: Managing the Risk of Supply Chain Attack.
Conclusion
Cybersecurity starts with an understanding of the threats that your organisation may face, and the options available to you to mitigate those risks. From there you can prioritise and focus your cybersecurity efforts with confidence.
For help protecting your business, speak with one of our cybersecurity experts today.
Microsoft 365 is the ideal platform to support and empower mission-driven nonprofit organisations, not least of all because Microsoft offers Microsoft 365 plans specifically designed for nonprofits. These plans are designed to provide the same high-quality technology and business tools that for-profit organisations use, but at a discount, making them accessible and affordable for nonprofits of all sizes.
Qualifying for Nonprofit Pricing
Needless to say, there are requirements that your organisation must meet in order to qualify for access to Microsoft nonprofit resources. In summary, your organisation must meet three eligibility criteria:
- Your organisation must be a legally recognised nonprofit or NGO. Specifically in Australia, this means that:
- Must operate on a not-for-profit basis and have a mission to benefit the local community.
- Must be non-discriminatory.
There are also guidelines around which employees may use the licenses based on their employee status and role in the organisation. These guidelines draw a distinction between paid employees and volunteers and between Grants (free licenses) and discounted licenses.
You can read more about eligibility on the Microsoft website.
Microsoft 365 Nonprofit Pricing
Finding the right Microsoft 365 plan for your nonprofit can appear confusing due to the multiple options available. In practice, it’s quite straightforward, and here we aim to simplify the process and guide you towards making an informed decision that aligns with your specific needs both in terms of functionality and budget.
Price isn’t everything, but as consumers, we often consider price before any other factor. So, as a quick start, let’s look at this handy table below to see how Microsoft 365 for nonprofit plans compare with one another on price, before moving on to consider features and functionality.
Pricing
| License | $AUD ex GST | Notes |
|---|---|---|
| Microsoft 365 Business Basic (Charity) | 0 | Free up to 300 users |
| Microsoft 365 Business Standard (Charity) | $4.50 | |
| Microsoft 365 Business Premium (Charity) | $8.20 | Free up to 10 users |
| Microsoft 365 E3 (Charity) | $14.20 | |
| Microsoft 365 E5 (Charity) | $34.10 | |
| Prices are monthly, annual commitment, $AUD ex GST as at January 2024 |
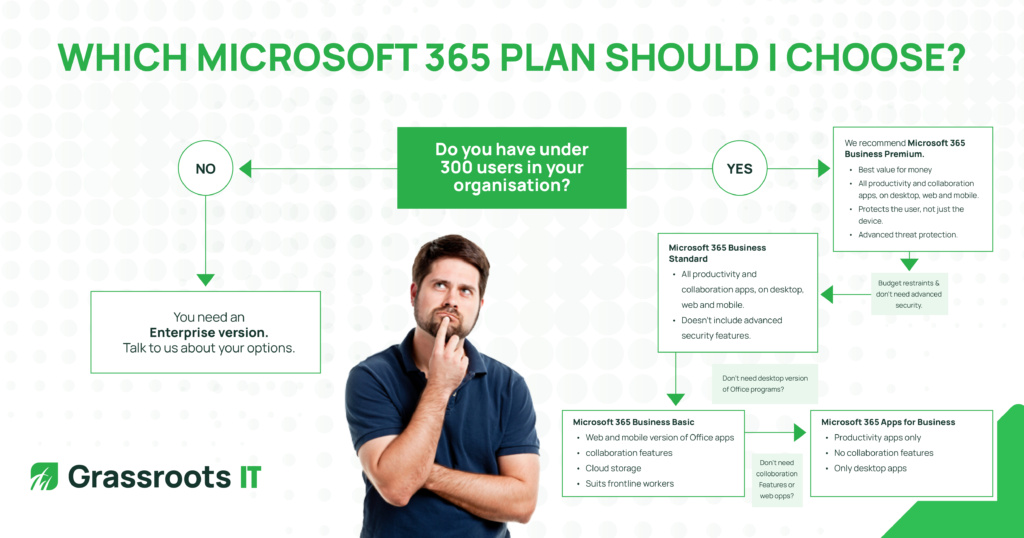
Microsoft 365 Business vs Enterprise
When deciding which Microsoft 365 plan is right for your non-profit, the first decision to consider is whether to choose a Business plan or an Enterprise plan. Thankfully this can be an easy decision for most, given that the Microsoft 365 Business plans support a maximum of 300 users.
Put simply, if you are a non-profit with more than 300 users, have a strong digital focus, require cybersecurity features, and solutions for compliance and governance, then the Microsoft 365 Enterprise Plans such as E3 and E5 will be the best fit.
On the other hand, if you are a non-profit with less than 300 users and looking to utilise the Microsoft 365 suite of business applications and are security conscious, then the Microsoft 365 Business Plans are your best option.
As a general rule of thumb for most nonprofit organisations (under 300 users) we recommend Microsoft 365 Business Premium due to the included features, primarily around cybersecurity & data protection.
Case Study Example
Care-Full Services is a growing non-profit, currently with 43 staff, operating out of one office location with multiple staff working from home. Front-line staff are often required to visit clients and frequently work remotely.
Team members need access to Microsoft Office applications including Outlook and Word, both on their laptops and mobile phones, and cloud storage services such as SharePoint to access business documents.
Team communication and collaboration is a high priority for leadership, particularly given so many of the team work remotely, so tools such as Microsoft Teams and Viva are important.
Cybersecurity is also becoming an increasingly urgent concern for the organisation, particularly given the sensitive nature of the information that is stored about clients and benefactors.
Care-Full Services decides to move to the Microsoft 365 Business Premium plan to provide the organisation with the most appropriate features to support the growth of the organisation while meeting immediate cybersecurity and collaboration concerns. They did consider Microsoft 365 Standard and Basic, but decided that the advanced security features, and access to the full suite of Office applications was important.
With Microsoft 365’s scalable pricing, Care-Full Services can scale up and down as the organisation grows or takes on new projects. Flexible plans and service offerings mean they can use the Microsoft 365 products and services that they need now and explore additional features later.
Other Microsoft 365 Business Plans
Microsoft does have other plans such as the Microsoft 365 Frontline Worker plan that may be suitable for your non-profit in certain situations, however these plans do have an extremely limited set of features and are best applied only in specific situations. For this reason, we don’t go into detail on these plans here in this post, however, may include them in any detailed recommendations that we offer on a case-by-case basis.
Find the right Microsoft 365 Plan for your Nonprofit
Before you make any decisions on a Microsoft 365 plan, the best thing to do is to start with assessing your organisation, its current and future goals. Grassroots IT has extensive experience working with nonprofit organisations and can assist you with evaluating your readiness for the move to Microsoft 365 and which plan would best suit your organisation to ensure a smooth, easy and rewarding experience.
Detailed Plan Inclusions
Microsoft 365 Business Premium (Charity)
Price: AUD $8.20 + GST per user/month
Ideal for: Non-profits with less than 300 users that require the latest Microsoft 365 applications as well as cloud services, email hosting, Microsoft collaboration tools plus more advanced cybersecurity defence and device management features.
Features include:
- Desktop and web versions of Outlook, Word, Excel, PowerPoint, and OneNote
- PC only version of Access and Publisher
- 50gb email storage
- Custom domain name
- Access to Microsoft Exchange
- Microsoft Teams – a chat-based collaboration hub that lets you host online meetings for up to 250 participants.
- SharePoint – Share and collaborate on files and content with your own organisational intranet.
- 1TB of OneDrive cloud storage
- Exchange Email Protection – protect organisation emails from spam, malware and known threats.
- Microsoft Bookings – allows customers to easily schedule appointments
- Advanced Threat Protection – Protect your organisation with Microsoft’s state of the art security defence against more sophisticated cyberattacks.
- Manage and control access to corporate files and data remotely
- Enforce malware protection policies to prevent future cyberbreach attacks
- PC and mobile device management
- Automatic Office 365 applications deployment to managed devices.
If you’re a non-profit that highly prioritises data security and cybersecurity, then a Microsoft 365 Business Premium Plan is your ideal option. You can get your always up-to-date Microsoft 365 essentials with cloud storage, integrated Microsoft business tools plus a highly advanced Microsoft defence system to give you peace of mind about the security of your data and resources. Have the ability to manage the devices that access your data and create policies to make sure that your business is protected against internal cyberattacks.
Microsoft 365 Business Standard (Charity)
Price: AUD $4.50 + GST per user/month
Ideal for: Non-profits with less than 300 users that require up-to-date versions of Office applications as well as cloud services, email hosting, and Microsoft collaboration tools, but do not need advanced cybersecurity protection or centralised device management.
Features include:
- Desktop and web versions of Outlook, Word, Excel, PowerPoint, and OneNote
- PC only version of Access and Publisher
- 50gb email storage
- Custom email domain name
- Access to Microsoft Exchange
- Microsoft Teams – a chat-based collaboration hub that lets you host online meetings for up to 250 participants
- SharePoint – Share and collaborate on files and content with your own organisational intranet
- 1TB of OneDrive cloud storage
- Exchange Email Protection – protect organisation emails from spam, malware and known threats
- Microsoft Bookings – allows customers to easily schedule appointments
The Microsoft 365 Business Standard Plan is perfect for your non-profit if you require the Microsoft Office 365 applications, as well as cloud storage and customised domain for your company email. This plan does not have the advanced security features of the Business Premium plan.
Microsoft 365 Business Basic (Charity)
Price: Free for up to 300 users.
Ideal for: Non-profits with less than 300 users that require web-only versions of Office applications as well as cloud services, email hosting, and Microsoft collaboration tools.
Features include:
- Web versions of Outlook, Word, Excel, PowerPoint, and OneNote
- 50gb email storage
- Custom email domain name
- Access to Microsoft Exchange
- Microsoft Teams – a chat-based collaboration hub that lets you host online meetings for up to 250 participants.
- SharePoint – Share and collaborate on files and content with your own organisational intranet.
- 1TB of OneDrive cloud storage
The Microsoft 365 Business Basic Plan is perfect for your non-profit if you require only web-based access to Office apps and cloud services and have no particular concerns about cybersecurity. In some situations, Microsoft 365 Business Basic can be a good fit for frontline works who only require a bare minimum of access to corporate systems.
Microsoft 365 E3 (Charity)
Price: AUD $14.20 + GST per user/month
Ideal for: A digital-driven organisation with more than 300 users that requires the essential Office 365 business tools, more storage options plus more powerful functionalities and integration between apps to keep up with the growing needs of the business using the help of Microsoft 365 enterprise technologies.
Highlight Features included:
- All features included in Microsoft 365 Business Premium Plan
- Enterprise-class Microsoft 365 applications
- Microsoft Teams – a chat-based collaboration hub that lets you host online meetings for up to 250 participants using the desktop or web applications
- OneDrive for Business (Talk to us about storage options)
- Windows Enterprise
- Microsoft Intune
- Microsoft Endpoint Configuration Manager
- Windows Autopilot
- Azure Active Directory Premium Plan 1
- Microsoft Endpoint Configuration Manager
- Microsoft 365 data loss prevention
- Windows BitLocker
- Microsoft Security and Compliance Center
- Microsoft 365 Admin Center
- Microsoft Advanced Threat Analytics
- Advanced organisational productivity insights with MyAnalytics
- Azure Information Protection P1
Having a Microsoft 365 E3 Plan in your non-profit means that your organisation has the right tools to move forward with a more collaborative approach. With fully integrated applications and administration tools in the bag, Microsoft 365 E3 enables you and your organisation to work more efficiently while maintaining the security of your corporate data.
- test
- test with number
- test with number
- test with number
- test
- test
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
In today’s digital era, cybersecurity threats are an ever-present and evolving danger. Organisations, regardless of size, are at constant risk of cyberattacks, including ransomware and data breaches. The increasing sophistication of these threats demands an advanced level of vigilance and response, which brings Managed Detection and Response (MDR) into the spotlight.
What is Managed Detection and Response (MDR)?
MDR is a comprehensive cybersecurity service that offers round-the-clock monitoring and response to cyber threats. It’s not just another line of defence; it’s a strategic approach that combines technology, processes, and importantly, human expertise to identify and mitigate cyber risks effectively. Although an oversimplification, it may be helpful to consider MDR as being a combination of SIEM (security monitoring & alerting) + security software (such as endpoint protection agents) + SOC (A team of security experts on standby to respond).
To better understand this, it can help to consider where MDR fits in relation to other alternative approaches to cybersecurity. To illustrate this we will compare MDR to three other common offerings: Unmanaged cybersecurity, Cybersecurity managed by an MSP/TSP and finally a specialist Managed Security Services Provider (MSSP) engagement.
Unmanaged Cybersecurity
Unmanaged cybersecurity generally involves having one or more basic cybersecurity products deployed, such as endpoint protection agents, but without any oversight or management of those products, or any broader cybersecurity strategy. Cybersecurity products are likely configured with default settings and may or may not be functioning effectively. In the event of a cybersecurity incident, the organisation will likely remain oblivious until it’s far too late and significant damage is done.
By comparison MDR will be more expensive but will also be far more effective in protecting the organisation. MDR will not provide a holistic cybersecurity strategy or oversight for the entire organisation, so security gaps are likely to remain, but for the areas where MDR is deployed, security will be tight, and responses to any potential incidents will be rapid.
MSP Managed Cybersecurity
Of the scenarios presented here, the most common is where the organisation engages a Managed Services Provider (MSP) to provide not only cybersecurity services, but other IT services such as end-user helpdesk and cloud services. Commonly the MSP will help with cybersecurity strategy and the deployment of various cybersecurity products and controls, as well as the ongoing management of these solutions.
The existence of a broader cybersecurity strategy and oversight means that gaps in protection are less likely, compared to unmanaged cybersecurity, but still not entirely ruled out. The MSP will respond to any cybersecurity incidents detected, however is unlikely to respond as rapidly as an MDR solution would, nor with the same deep level of technical expertise that and MDR brings. The ideal scenario is to engage both an MSP and an MDR solution.
MSSP Managed Cybersecurity
A Managed Security Services Providers (MSSPs) operates on a similar model to an MSP but with a narrow focus on cybersecurity. They will bring a deep level of technical expertise, with a team of dedicated security analysts and engineers. The MSSP’s response to any detected incident will likely be faster and more technically capable than that of an MSP due to the specialised nature of its services.
Engaging with a specialist MSSP can provide a level of security and response that surpasses both MSP and MDR solutions, but this comes at a higher cost. Additionally, MSSPs may not have the same level of understanding or familiarity with an organisation’s unique IT environment compared to an MSP who has been managing their IT services for some time. For organisations requiring this level of cybersecurity response, engaging both an MSP and an MSSP to work closely together will provide the best outcome.
The Advantages of Managed Detection Response (MDR)
Managed Detection & Response offers several unique advantages that set it apart from other common cybersecurity solutions.
- Continuous Monitoring and Rapid Response: Cyber threats don’t adhere to a 9-to-5 schedule. MDR provides 24/7 monitoring, ensuring that threats are identified and addressed promptly, often within minutes. Many other cybersecurity offerings may monitor 24×7, however responding to incidents may take signification longer.
- Expertise and Specialisation: MDR services are not simply automated technology but are manned by cybersecurity experts who specialise in threat detection and response, bringing a level of expertise that other purely automated solutions can’t match.
- Advanced Technologies and AI Integration: MDR services leverage advanced technologies, including Artificial Intelligence (AI) and Machine Learning (ML), to enhance threat detection capabilities.
- Customisation and Scalability: MDR solutions can be tailored to fit the specific needs of an organisation, scaling as the organisation grows or as threats evolve. Many other comparable cybersecurity solutions are either too large and expensive for many organisations or alternatively may fail to scale effectively beyond a certain size.
- Cost-Effectiveness: Building and maintaining a comparable in-house security operation can be prohibitively expensive, whether this in-house team is your own, or run by your main technology partner or MSP. MDR services offer a cost-effective alternative, providing top-tier security expertise without the overhead of in-house or boutique engagements.
The Role of Managed Detection Response (MDR) in Modern Business
MDR services play an extremely important role in modern business, addressing business and security requirements that many other cybersecurity solutions cannot.
Protecting Against Ransomware and Data Breaches
Ransomware attacks and data breaches can have devastating effects on businesses. MDR plays a critical role in not only preventing these attacks but also in minimising the impact if they occur, with 24×7 human lead incident response.
Addressing the Cybersecurity Talent Shortage
The cybersecurity industry faces a significant talent shortage. MDR services help bridge this gap by providing access to an extensive team of experts, thus alleviating the pressure on in-house resources, or avoiding the rapidly increasing costs of boutique cybersecurity providers.
Compliance and Regulatory Requirements
Many industries face stringent regulatory requirements regarding data protection and cybersecurity, not to mention increasing challenges in qualifying for cyber insurance coverage. MDR services help ensure compliance with regulations, avoiding potential legal and financial penalties, while helping to satisfy insurers’ stringent requirements.
Managed Detection Response (MDR): The Human Touch
While technology is a critical component of MDR, the human element is what sets MDR services apart from other purely product-based cybersecurity solutions. Skilled cybersecurity professionals bring a level of intuition and experience that cannot be replicated by machines alone.
MDR teams comprise individuals with diverse backgrounds in cybersecurity, offering a blend of skills that range from threat hunting to incident response. This human oversight ensures that the subtleties of cyber threats are not overlooked.
Effective MDR services foster collaboration between the service provider and the client. Regular communication and reporting ensure that clients are aware of their security posture and any actions taken on their behalf.
The Future of Managed Detection Response (MDR)
Looking ahead, the role of MDR in cybersecurity is only set to grow. As cyber threats become more sophisticated, the need for comprehensive, responsive, and expert-driven cybersecurity solutions will become more pronounced.
As new technologies emerge, MDR services will evolve to incorporate these advancements, further enhancing their threat detection and response capabilities.
Conclusion
Managed Detection and Response represents a significant advancement in the field of cybersecurity. It offers a dynamic, expert-driven solution to the complex and ever-changing landscape of cyber threats. For businesses looking to bolster their cybersecurity posture, MDR presents a comprehensive, effective, and adaptable solution, ensuring peace of mind in an increasingly digital world.
Tips on choosing the right Microsoft 365 plan for your business
Understanding Microsoft 365 pricing is crucial when navigating the various options and selecting the right plan for your business. In this blog post, we’ll help you cut through the confusion, simplify the choices and guide you to make the most informed decision based on your business needs!
Price isn’t everything, but as consumers we often consider price before any other factor. So let’s look at this handy table below to see how the Microsoft 365 for Business plans compare with one another:
Note: This article covers Microsoft 365 commercial pricing. If you are a nonprofit, click here to learn more about Microsoft 365 Nonprofit pricing.
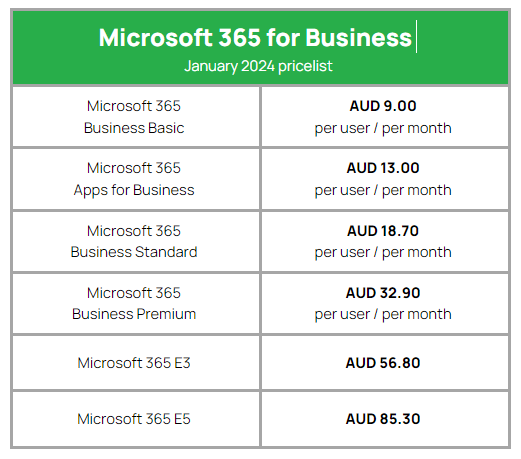
^^Please note these costs are monthly, but based on an annual commitment, and do not include GST.
Now that you have an idea of the costs involved, let’s dive into the features that you get from each plan.
All business and enterprise plans of Microsoft 365 (previously Office 365) come with the Office applications that are vital for any business. However, the Business Plans cater for a maximum of 300 users. If your organisation has more than 300 users, an Enterprise Plan is what you should be looking for.
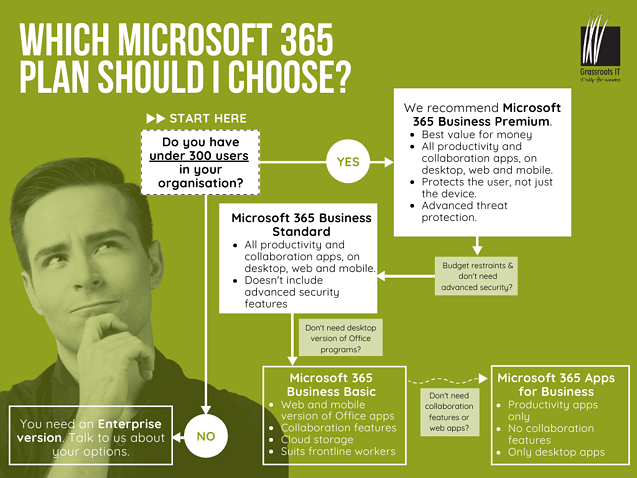
Here’s a breakdown of the main features included in each plan, starting off with the Microsoft 365 Business Plans:
Microsoft 365 Business Premium
Price: AUD $32.90 + GST per user/month
Ideal for: Businesses with less than 300 users that require up-to-date versions of Office applications as well as cloud services, email hosting, Microsoft collaboration tools plus more advanced cybersecurity defence and device management features.
Features include:
- Desktop and web versions of Outlook, Word, Excel, Powerpoint, and OneNote
- PC only version of Access and Publisher
- 50gb email storage
- Custom domain name
- Access to Microsoft Exchange
- Microsoft Teams – a chat-based collaboration hub that lets you host online meetings for up to 250 participants
- Sharepoint – Share and collaborate on files and content with your own organisational intranet
- 1TB of OneDrive cloud storage
- Exchange Email Protection – protect organisation emails from spam, malware and known threats
- Microsoft Bookings – allows customers to easily schedule appointments
- Advanced Threat Protection – Protect your organisation with Microsoft’s state of the art security defence against more sophisticated cyberattacks.
- Manage and control access to corporate files and data remotely
- Enforce malware protection policies to prevent future cyberbreach attacks
- PC and mobile device management
- Automatic Office 365 applications deployment to managed devices
If you’re a business that highly prioritises data security and cyberbreach prevention then a Microsoft 365 Business Premium Plan has everything you need. You can get your always up-to-date Office 365 essentials with cloud storage, integrated Microsoft business tools plus a highly advanced Microsoft defence system to give you peace of mind about the security of your data and resources. Have the ability to manage the devices that access your data and create policies to make sure that your business is protected against internal cyberattacks.
Microsoft 365 Business Standard
Price: AUD $18.70 + GST per user/month
Ideal for: Businesses with less than 300 users that require up-to-date versions of Office applications as well as cloud services, email hosting, and Microsoft collaboration tools.
Features include:
- Desktop and web versions of Outlook, Word, Excel, Powerpoint, and OneNote
- PC only version of Access and Publisher
- 50gb email storage
- Custom email domain name
- Access to Microsoft Exchange
- Microsoft Teams – a chat-based collaboration hub that lets you host online meetings for up to 250 participants
- Sharepoint – Share and collaborate on files and content with your own organizational intranet
- 1TB of OneDrive cloud storage
- Exchange Email Protection – protect organisation emails from spam, malware and known threats
- Microsoft Bookings – allows customers to easily schedule appointments
The Microsoft 365 Business Standard Plan is perfect for your business if you require all the up-to-date Office 365 applications, as well as cloud storage and customised domain for your company email. This plan does not have the advanced security features of the Premium plan.
Alternatives to Office 365 for business
If you’re just looking to utilise the core functions of Office 365, which includes web and mobile versions (no desktop versions) of the Office 365 apps with 50gb mailbox allocation and 1 TB cloud storage in OneDrive, an alternative option is the Microsoft 365 Business Basics plan. This is best suited for frontline workers who aren’t sitting at a desk and therefore don’t have need for desktop versions of the Office 365 apps. It includes the productivity apps (Word, Excel, Powerpoint) as well as the collaboration apps (Teams, Sharepoint, OneDrive, Exchange).
Last on the list of the Microsoft 365 Business plans is the Microsoft 365 Apps plan which can provide for your basic Office application needs (desktop, web and mobile versions of Word, Excel, Powerpoint and Outlook) with OneDrive storage access to let you keep your files in the cloud. Basically, it’s a basic apps-only plan. On this plan, there is no shared email (via Exchange) or collaboration features (like Teams or Sharepoint).
Now that the Business Plans are covered, let’s move on to the Microsoft 365 Enterprise Plans. If what you need is a more robust solution for your growing organisation, these Enterprise plans offer a wider spectrum of functionalities and a higher user limit that you won’t find in the Microsoft 365 Business Plans.
Microsoft 365 E3
Price: Contact Us for Pricing
Ideal for: A digital-driven organisation with more than 300 users that requires the essential Office 365 business tools, more storage options plus more powerful functionalities and integration between apps to keep up with the growing needs of the business using the help of Microsoft 365 enterprise technologies.
Highlight Features included:
- All features included in Microsoft 365 Business Premium Plan
- Enterprise-class Microsoft 365 applications
- Microsoft Teams – a chat-based collaboration hub that lets you host online meetings for up to 250 participants using the desktop or web applications
- OneDrive for Business (Talk to us about storage options)
- Windows Enterprise
- Microsoft Intune
- Microsoft Endpoint Configuration Manager
- Windows Autopilot
- Azure Active Directory Premium Plan 1
- Microsoft Endpoint Configuration Manager
- Microsoft 365 data loss prevention
- Windows BitLocker
- Microsoft Security and Compliance Center
- Microsot 365 Admin Center
- Microsoft Advanced Threat Analytics
- Advanced organisational productivity insights with MyAnalytics
- Azure Information Protection P1
Having a Microsoft 365 E3 Plan in your business means that your organisation has the right tools to move forward with a more collaborative approach. With fully integrated applications and administration tools in the bag, Microsoft 365 E3 enables you and your organisation to work more efficiently while maintaining the security of your corporate data.
How do I decide whether to buy a Business Plan or an Enterprise Plan?
Put simply, if you’re a business with 300 or less users and looking for solutions to start your move to the cloud and migrate data, utilise the Office 365 suite of business applications and are security conscious, then one of the Microsoft 365 Business Plans is your best option.
If you’re an organisation with more than 300 users, that has a strong digital focus, requires cybersecurity features, as well as solutions for compliance and governance, then the Microsoft 365 Enterprise Plans may prove a more effective solution for you.
Case example:
Acme Engineering is a growing business, currently with 57 staff, operating out of two office locations. Engineering staff are often required to travel and work from remote locations.
Team members need access to Office application, both on desktop and mobile versions, and cloud storage services.
They are also working towards promoting a more positive collaboration culture and are interested in using the features available in Teams, such as video calls, file sharing and project collaboration.
Some of the staff are bringing their own devices to do their job and cybersecurity is a priority for the business, therefore they require advanced cybersecurity defences and device management options.
Acme Engineering decides to move to Microsoft 365 Business Premium plan which can provide the business with the appropriate features to support the growth of the organisation.
One important thing to mention is that Microsoft plans are both flexible and scalable. With scalable pricing, you can scale up and down as your business grows or you take on projects. Flexible plans and service offerings mean you can use Microsoft 365 products and services that you need now and explore additional features later. You can even mix and match to suit different staff requirements.
Find the right Office 365 plan for your business
Before you make any decisions on a Microsoft 365 plan, the best thing to do is to start with assessing your organisation, its current and future goals. Seek the help of an expert to assist you with evaluating your readiness for the move to Microsoft 365 and which plan would best suit your organisation to ensure a smooth, easy and rewarding transition.
If you’d like more information, get in touch with the Grassroots IT team on 1300 554 138 or contact us online.
Technology and the internet play a crucial role in the day-to-day operations of non-profit organisations of all sizes, from small volunteer-run operations to huge worldwide groups like the Red Cross. From fundraising to communication with donors and volunteers, technology has made these tasks more efficient and effective. However, this increased use of technology also brings about heightened risks of cybersecurity threats.
According to statistics from the 2020 Global Risk Report by the World Economic Forum, cyberattacks are among the top 5 global risks in terms of likelihood. This means that organisations, including non-profits, need to take cybersecurity seriously in order to protect their assets and data.
The unique cybersecurity challenges for non-profits
Not only are non-profit organisations often handling sensitive data, such as donor and beneficiary details, but they may also be responsible for substantial funds, making them an attractive target for cyber criminals. Add to this that many non-profits operate with smaller teams and budgets, and it becomes clear that many may face unique challenges when it comes to cybersecurity.
Unfortunately, many non-profit organisations are ill-prepared to handle cyber threats, leaving them vulnerable to attacks with potentially devastating consequences, such as:
Financial Loss
A successful cyberattack on a non-profit can result in direct financial losses from stolen funds or ransomware, not to mention costs involved in recovering from the incident and returning operations to normal. This can be particularly damaging for smaller non-profits with limited resources, or those without cyber-insurance coverage.
Reputational Damage
The loss of sensitive data, especially if it involves personal or financial information of donors and beneficiaries, can severely damage the trust and confidence placed in the organisation. This could result in a loss of supporters and volunteers, making it harder for non-profits to achieve their goals.
Legal & Compliance Consequences
Non-profits are also held to the same legal and compliance standards as for-profit organisations when it comes to protecting sensitive data. Failure to comply with these regulations could result in legal consequences, fines, and reputational damage.
Low-cost cybersecurity strategies for non-profit organisations
Given the competing priorities of increasing risks of cyber threats and staying focussed on mission, it is important for non-profit organisations to make the most of effective, right sized and cost-efficient cybersecurity strategies. Here are some key strategies that we have had success with when working with non-profit clients to improve their cybersecurity.
Employee training & awareness
One of the most vulnerable areas of any organisation’s cybersecurity is its employees. It is crucial for non-profits to provide cybersecurity awareness training to all staff members, including volunteers, on safe internet practices and how to identify potential threats.
As well as commercially available cybersecurity awareness training offerings, there are plenty of free resources available online, such as on YouTube. Running internal training sessions and information sharing workshops is also free and easy, and an excellent way of building cybersecurity awareness amongst staff and volunteers.
Read more: Building a culture of cybersecurity awareness
Vendor donations & discounted software
Non-profits can take advantage of vendor donation programs to obtain a range of technology solutions including cybersecurity software and tools either at a reduced price or for free. Many technology companies such as Microsoft, Canva and Xero have programs specifically designed for non-profits that offer discounted or donated products and services.
As an example of what’s available, Microsoft offers up to 10 free licenses of Microsoft 365 Business Premium to qualifying non-profit organisations in Australia, with deep discounts for additional licensing over the initial 10. How can this help non-profit cybersecurity? Microsoft 365 Business Premium includes many advanced cybersecurity features that other plans do not. Without these discounts many non-profits would be forced to rely on cheaper alternatives, missing out on important security & data protection benefits.
Partners that understand non-profits
When selecting a non-profit technology partner, decision makers should consider companies that understand the unique challenges and needs of non-profit organisations. IT partners who are well-versed in the non-profit sector are not just vendors; they are collaborators who align closely with the mission and values of the non-profit.
This alignment is crucial, as it translates into more than just technical support – it’s about providing cost-effective and mission-driven solutions. The right IT partner is not just a service provider but a strategic ally – one that empowers the non-profit to focus on their core mission, knowing that their technology needs are in capable and understanding hands. This is important to ensure that non-profit cybersecurity solutions are carefully considered and right sized for the unique needs of the organisation, taking into consideration the organisational strategy, key risk areas and various constraints.
Don’t neglect the fundamentals
While it may seem that advanced technology is the key to cybersecurity, organisations should not neglect the fundamentals. Simple measures like regular data backups and regular updates of software and operating systems can go a long way in preventing cyberattacks.
Additionally, having strong password policies and enforcing multi-factor authentication will also add an extremely effective layer of security. These measures are often low-cost or even free, making them easily accessible for non-profits with limited budgets.
The importance of robust cybersecurity measures for non-profits
While non-profit organisations may face unique challenges in the realm of cybersecurity, there are also a variety of strategies and resources available to help them improve their defenses. Grassroots IT has deep expertise working with non-profit organisations and understands the importance of providing cost-effective solutions that align with their missions and values. To speak with a non-profit technology expert, contact us today.
Updated 19 January 2024 with new licensing details.
2023 has well and truly been the year of Generative Artificial Intelligence, triggered by the release of ChatGPT in November 2022. Not only have we seen an entire wave of AI based start-ups spring into existence, but big players like Meta and Google have also launched their own offerings.
Without doubt though, the latest technology to make waves in the business world is Microsoft Copilot – an AI-powered tool set to be embedded into almost every Microsoft app from Windows to PowerPoint to Dynamics CRM.
With a surge of interest and early adopters already on board, it’s essential to understand how to prepare your business for Microsoft Copilot to not only maximise the return on your investment, but also to avoid potentially unforeseen complications that may arise.
What is Microsoft Copilot?
Microsoft Copilot is an AI-powered tool that uses machine learning to assist users in completing tasks within various Microsoft apps. It has been designed to help with a range of tasks – from writing emails and creating slides, to managing your calendar and organising data. If you’re at all familiar with other interactive, chat-based AI tools such as ChatGPT then you will be comfortable with Copilot.
Why is Microsoft Copilot Important for Businesses?
It’s fair to say that AI offers huge potential benefits for businesses of all sizes. But what specifically is the importance of Microsoft Copilot?
Microsoft Copilot offers a wide range of benefits for businesses, including increased efficiency and productivity, higher quality outputs, and improved accuracy. By automating repetitive tasks and providing helpful suggestions, it can save employees time and reduce human errors.
More importantly though, Copilot offers a number of features that no other AI tool can match:
1. Deep Integration
Copilot has been specifically designed to work seamlessly with commonly used Microsoft apps, such as Outlook and PowerPoint, meaning there is no need for users to switch between multiple platforms. Imagine opening up PowerPoint and instructing Copilot to “Create a 10-slide deck on next year’s investment strategy.”
2. Access to corporate data
With Copilot deeply embedded within the Microsoft cloud, it can have secure access to all of your existing corporate data stored not only in Microsoft 365, but other third-party cloud apps. This means that Copilot can provide personalised responses based on your company’s own data, not just the generally available public information that other AI tools are limited to.
3. Privacy and Security
Microsoft has always been at the forefront of privacy and security, and Copilot is no exception. All data used by Copilot is stored securely within the Microsoft cloud and is subject to strict privacy policies and existing security rules. Copilot will not make your data available to anyone who does not already have access to it.
The risks of adopting Microsoft Copilot
While the benefits are clear, it’s important for businesses to understand and mitigate any potential risks associated with implementing Microsoft Copilot. Many of these risks are best-practice considerations already but are worth revisiting before considering a Copilot deployment:
1. Poor user adoption
It’s important to remember that Copilot is an AI tool and therefore requires some level of training in order to use it effectively. Additionally, there may be a learning curve for employees as they get used to using Copilot and may need support during this transition period. A well-planned training and change management program can help mitigate these risks.
2. Data privacy
Copilot operates within the context of the user, meaning that Copilot will respect any security restrictions that exist around what corporate information the user can and cannot access. Copilot will not surface information that the user would not otherwise have had access to. This does however put the onus back on the business to ensure that all data is properly restricted to only those who should have access.
3. Governance & compliance
With the use of AI in businesses becoming increasingly common, it’s important for organisations to have a good understanding of how Copilot is using their data. A governance and compliance plan should be put in place to ensure that all data used by Copilot is compliant with existing regulations and policies.
Preparing for Microsoft Copilot
So, what should businesses do to prepare for the adoption of Microsoft Copilot? There are three key issues that need to be addressed:
1. Microsoft 365 Licensing
The first step is to ensure that your organisation has the appropriate Microsoft 365 licenses in place to support Copilot. This means that you must be using one of the following Microsoft 365 license types. Our recommendation for most organisations is Microsoft 365 Business Premium.
- Business Standard
- Business Premium
- E3
- E5
Copilot itself will require an additional per-user license costing approximately AU$540 per user for an annual license. At this stage there is no month-to-month purchase option available, only annual. Please also note that there is no non-profit pricing available at this stage.
2. Application Deployment & Adoption
Copilot requires the latest Microsoft 365 desktop apps such as Outlook and Word, so if you don’t already have these apps deployed & in use across your organisation, you will need to address this before deploying Copilot. Don’t forget to also consider user adoption. You can’t unlock productivity gains if no-one is using your new productivity tools.
Equally as important is where your corporate data is stored. Copilot is a cloud service, and your data must be in the cloud for it to be accessible. If you haven’t yet migrated your data into SharePoint, OneDrive, or some other cloud service accessible via Copilot Plugins, you will not be able to receive the full benefit of Copilot.
3. Data Security
The power of Copilot is in its ability to ingest your corporate data and provide intelligent, insightful responses. However, this also means that you must ensure your data is properly secured and only accessible to those who need it, lest you find information inappropriately surfaced to those who shouldn’t, but do, have access.
Microsoft 365 is extremely good at automatically surfacing relevant and related content. This can be handy when, for example, Outlook presents you with a list of documents related to your upcoming meeting. Of course, it will only show you documents that you already have permission to access, but there-in lies the potential for problems, when documents may not have been properly secured to only those people that truly need access.
Conclusion
Microsoft Copilot offers a wealth of benefits for businesses, from increased productivity and efficiency to improved accuracy and access to personalised data. As with any new technology, there are potential risks to consider and prepare for, such as user adoption and data privacy.
If you would like to talk about preparing your business for Copilot, contact us today.
At Grassroots IT our mission is to help our clients drive meaningful change through the effective, strategic use of technology. A key part of this is understanding our client’s IT budgets and helping them to get the most bang for their buck while avoiding some common IT investment mistakes.
IT may be an essential and unavoidable cost of doing business, but with appropriate planning, your IT budget can help drive your business forward rather than simply maintaining the status quo. To achieve this however appropriate thought and planning must be devoted to IT investment decisions so as to avoid these common mistakes.
Failing to align IT investments with business goals
One of the biggest mistakes that we see organisations make is investing in IT solutions without proper consideration of how those investments align with their business goals. The role of IT in any organisation is to support the overall business strategy, and with a limited IT budget, every dollar must be spent to directly impact that result in a positive way.
A clearly articulated IT Strategy aligned with the overall business goals and financial strategy is a must-have for any organisation and will help to ensure that all IT investments are made with a clear understanding of how they will contribute to achieving the desired business outcomes.
Some potential areas of IT spending that tend to align strongly with business outcomes can include:
- IT Support – to ensure that systems are running well, and help is on hand when required.
- Cybersecurity – to protect the organisation from damaging data loss.
- Staff training – to optimise staff satisfaction & productivity.
- Process Automation – to increase productivity & improve customer service.
Related: Three Crucial Elements for your IT Strategy
Neglecting change management
Another mistake that we see is failing to implement proper change management processes when adopting new technology. For IT investments to be successful, employees need to understand why the investment is being made and how it will benefit them. This requires clear communication and training, as well as providing appropriate support during the transition.
Too many organisations will implement new technology without properly preparing their staff, leading to resistance and low adoption rates. This can result in wasted investment, lost productivity and a lack of return on the IT spend.
How do you avoid this mistake? Adopt a mindset of taking your team on the journey with you. Explain why the new technology is being implemented, consult with key stakeholders when designing the solution, and provide staff with training and support on the new system so that they can become comfortable and productive as quickly as possible. The more buy-in employees have along the way, the more likely the IT investment will be successful.
Overlooking new ways of working
With change comes opportunity, yet too many organisations fail to see the potential of new technologies and ways of working, even after implementation! It’s not uncommon for an organisation to adopt a new technology without fully reviewing its work practices to take the best advantage of the new platform. Although this may feel safe and comfortable, it risks leaving significant value on the table.
One common example that we see is organisations that adopt the Microsoft 365 platform yet continue to use apps such as Zoom and Dropbox despite these same features being not only available but better integrated within Microsoft 365. Through a simple process of training staff on these Microsoft 365 features and updating business processes, not only would the business save money on app subscriptions, but users would have a more streamlined and productive experience.
So how do you avoid this mistake? Regularly review your work processes and practices after implementing a new technology. See how you can streamline workflows and improve efficiency by utilizing the full capabilities of the new platform. This may also involve training staff on these new features so that they are aware of all the tools at their disposal and can help identify opportunities for new and improved ways of working.
Conclusion
Every organisation invests in its IT systems, but not all organisations focus on maximising the ROI of that IT investment. By avoiding these common IT investment mistakes, you can be confident that your IT budget will deliver maximum bang-for-buck.
If you would like to speak with us about maximising the ROI of your IT budget, contact us today.
Business process automation is becoming increasingly important in today’s fast-paced and competitive world. It allows businesses to streamline their operations, save time and resources, and ultimately increase their efficiency and profitability.
In this article, we will look at three real-life case studies of automation solutions that Grassroots IT has recently implemented for our clients. One key point that I would like you to take away from these case studies is that in many cases the most impactful automations are small and simple, such as automating a weekly report, or shifting a paper-based process to a digital form.
Redefining Staff Onboarding: How Automation Transformed a Complex Process
With over 600 staff across Australia, our client already had a comprehensive employee onboarding process for each new hire. Unfortunately, due to the complex and comprehensive nature of this process, it was proving to be a burden on staff to execute, and difficult to track, resulting in inconsistent quality and increasingly long processing times.
The project began by reviewing and understanding the existing manual process, identifying which business systems were involved, and who owned the process at various stages. From this an automated solution was designed and implemented, fully automating the onboarding of new staff members across multiple functions and business systems.
Starting with the initial request being logged by the Human Resources department, the new process not only automatically creates and configures all necessary user accounts but engages staff in other departments to complete necessary actions and provide additional information as required. The process culminates by emailing a welcome pack to the new employee with important information to help get them settled.
Not only is the new automated process on track to dramatically reduce processing times from days to just minutes, but also improve consistency and greatly reduce the risk of errors.
Automated Awareness: Powering Up Training Attendance Through Scheduled Updates
Surfacing the right information to the right people can sometimes be as simple as sending an automated report. In this case study our client maintains a list of scheduled training events in SharePoint but was finding that even though the information was readily accessible, many staff remained unaware of upcoming training opportunities. This was resulting in low attendance at events and misinformed frustration amongst staff at the apparent lack of training opportunities.
To address this concern, our client wanted to send a weekly email to all staff with the latest information on scheduled events. Our automation team was able to use Power Automate to automatically generate and send a weekly report to all staff, pulling information directly from the SharePoint list, and formatted to the client’s specification. This not only saved time for staff who were previously manually communicating the events schedule, but also increased awareness of training opportunities among employees.
From Paper to Power Apps: Automating Traveler Identification for Accuracy and Efficiency
Our Australian-based client often found themselves needing to collect identification details from international travellers, requiring a manual process of completing paper-based forms and photocopying identification documents such as international drivers’ licenses and passports. Not only was the process clumsy and inefficient, but it also exposed the business to potential errors and compliance issues.
To improve this process, our automation team developed a mobile application using Microsoft PowerApps that allows staff to collect customer identification details directly on their phones or tablets while meeting with the traveller. The app not only collects customer information, but also captures photographs of passports and licenses along with a digital copy of the customer’s signature. All confidential information is stored securely in the Microsoft cloud and is only accessible by authorised personnel.
Overall, the new automated app has greatly improved efficiency, reduced errors, and increased security of the confidential information our client collects.
Conclusion
As you can see from these three examples, automation doesn’t have to be complex to make a big impact on business processes. In fact, a great place to start is by asking these two questions:
- What forms do we fill out on paper?
- What things do we do over and over again?
By identifying areas where manual tasks can be automated, you can save time and resources, increase efficiency, and ultimately improve your bottom line. If you would like to explore ideas for process automation, contact us today.


