Defining your IT strategy is a powerful step towards success, yet alarmingly we still find organisations that don’t take the time to clarify what they expect or require from IT. At its simplest your IT strategy is a statement of how you intend to use IT to support your over-arching business goals. You don’t have unlimited resources to spend on IT, so your IT strategy is there to clarify where you will focus your efforts, and equally as important where you will not.
In our work with clients formulating and executing on their IT strategies we often see clear trends emerging over time in response to the ever-changing IT landscape. Of course, every company will have their own unique IT strategy, but common patterns can emerge.
As we work with our clients in preparation for the year ahead, we are seeing the following three themes appearing with consistency.
Related: Why aligning your IT strategy with business goals is critical for success
User Experience
In response to the pandemic the world of work has changed significantly, also significantly shifting how people relate to their employment, the environments they work in, and the tools that they are expected to use. Simply put, user experience has become a critical element in every IT strategy.
But what does this mean for your organisation? It means that employees are expecting easy-to-use, efficient and user-friendly technology solutions that allow them to do their job effectively from any location. This includes everything from remote working tools to cloud-based collaboration platforms, all accessible as easily from their smartphone as their home office.
They are also expecting to have fingertip access to the information and expertise that they need, with top-tier training and support services available when required.
So, as you plan your IT strategy for 2024, make sure that user experience is at the forefront of your decision making and investment plans. Put yourself in the shoes of your employees and consider their daily tasks and interactions with technology – are they seamless, intuitive and empowering? If not, it’s time to make some changes.
Cybersecurity
As technology continues to evolve and become increasingly intertwined with our daily lives, the risk of cyber-attacks and data breaches has also risen exponentially. Cybersecurity is no longer just a concern for IT departments but should be a top priority for every organisation’s IT strategy, with direct board-level oversight.
A strong cybersecurity plan should include regular security audits, employee training on identifying and handling potential threats, as well as implementing the latest security software and protocols. Importantly in the post-pandemic world, your cybersecurity plan must also consider new ways of working. With many staff now working from home, old ways of securing your organisation may no longer be as effective.
Cybersecurity not a one-and-done task, but an ongoing process that must be continuously monitored and updated to stay ahead of potential threats. Make sure that your IT strategy reflects this and allocate appropriate resources to keep your organisation’s data safe and secure.
AI & Automation
2023 was the year that artificial intelligence hit the mainstream, with the release of ChatGPT throwing the floodgates open. The new-found accessibility of AI is emerging as an inflection point on the longer-term trend of business process automation, with the combination of the two promising significant opportunities.
AI and automation can streamline processes, improve efficiency, and reduce costs in almost every area of your organisation – from customer service to HR to supply chain management. It can also provide valuable insights and data analysis that humans may miss. As the technology continues to advance, it will only become more powerful and integrated with our daily lives.
It’s no longer a question of if but when AI and automation will become an integral part of every IT strategy. So, in the year ahead, make sure that you’re keeping up with the latest developments and considering how it can enhance your organisation’s operations and drive growth.
Conclusion
As we move towards 2024, it’s clear that user experience, cybersecurity and AI/Automation will continue to be pivotal elements of every IT strategy. Organisations must prioritize these areas to stay competitive and meet the evolving needs of their employees and customers. With a strong focus on these essential components, your IT strategy can serve as a roadmap for success in the ever-changing digital landscape.
Keep in mind, however, that these are just three of many elements to consider when crafting your IT strategy. As technology continues to advance, new challenges and opportunities will arise, requiring organisations to stay agile and adaptable.
Grassroots IT has many years of experience working with clients to formulate IT strategies that align with business goals and lead to tangible results. If you would like to talk about your IT strategy, contact us today.
As technology continues to advance, the role of automation in business processes is becoming increasingly crucial, at the same time as the complexity and cost of automation rapidly falls. What used to be the domain of large organizations with deep pockets is now easily accessible to small and medium-sized businesses thanks to a raft of cloud technologies such as Zapier and Power Automate.
The benefits of automation are numerous and can greatly impact a company’s efficiency, quality, and bottom line. Let’s explore some of the key advantages of incorporating automation into your business processes.
What is Business Process Automation?
Business process automation (BPA) is the use of technology to automate repetitive, routine tasks in a business. This can include anything from simple data entry and document processing to complex workflows and decision-making processes.
By automating these tasks, businesses can save time, reduce errors, and free up employees to focus on more important and strategic work. This not only increases productivity but also allows for better utilization of resources and streamlines operations.
The Benefits of Automating Business Processes
Automation ultimately can help with two things – reducing costs (money, time) and improving quality (errors, consistency). But how does that translate into broader business benefits? Here are some examples.
Reduced errors and rework
Human error is inevitable, but it can be costly for businesses. Automating a process can greatly improve the quality and accuracy of the output, drastically reducing the chances of errors and inconsistencies that result in costly rework. This is especially important for tasks that require a high level of accuracy or data input, such as financial calculations or data analysis.
Enhanced customer service
By automating tasks, businesses can provide faster and more consistent service to their customers. For example, automated order processing can reduce the time it takes for customers to receive their orders, resulting in a better overall customer experience.
Increased efficiency and productivity
Automation allows for tasks to be completed faster and more accurately, resulting in increased efficiency and productivity. This is particularly beneficial for businesses dealing with high volumes of repetitive tasks, such as data entry or order processing. By automating these tasks, employees can focus on more valuable work that requires human input and decision-making.
Scalability and flexibility
As your business grows and evolves, so do your processes. With automation, these processes can easily be adapted and scaled up or down to meet the changing needs of your business. This allows for greater flexibility and agility, resulting in faster response times and improved customer satisfaction without the need for additional manpower.
Identifying Opportunities for Automation
Your organisation will have plenty of opportunities for automation – I guarantee it. So how best to get started? The first step in incorporating automation into your business processes is identifying tasks and workflows that can benefit from it. When reviewing your current processes, keep an eye out for any of these characteristics that are good indicators that your process may be ripe for automation.
- Repetitive & rules based.
- High volume of transactions.
- Data intensive.
- Time sensitive.
- Prone to error or requires a high degree of consistency.
- Passes data between multiple systems.
- Relies on paper-based forms or rekeying data ‘back at the office’.
Every department is a candidate to benefit from automation, from back-office functions such as Finance & Admin, to Sales & Marketing, Customer Service and all points in-between. Watch closely for processes that consistently bottleneck at the same stage to see if automation could clear the way.
Listen carefully to when people actually use the word “process” as they speak, such as “We’re busy processing the purchase orders”. Pay particular attention to those job roles that involve a lot of data entry and be aware of when frustrations bubble over because someone isn’t properly “following the process”. All of these can be ideal opportunities to bring automation into play.
The Future of Business Process Automation
As technology continues to advance, the possibilities for automation are endless. With the emergence of artificial intelligence (AI) and machine learning, processes that were once thought to be too complex or unpredictable for automation can now be automated with high accuracy. This means even greater potential benefits for businesses in terms of productivity, quality and cost savings.
Conclusion
Best of all, business process automation is now easily within reach of organisations of all sizes. If you’d like to explore the opportunities for automation, contact us today.
The question of whether you should be backing up your Microsoft Office 365 data will often illicit passionate arguments from both sides. On one hand, you have those who argue that Microsoft 365 already has built-in backup and disaster recovery features, making an additional backup unnecessary. On the other hand, you have those who swear by Office 365 backups as a necessary precaution against potential data loss.
But what is the truth? Is backing up your Microsoft 365 data necessary or is it all just a conspiracy by software vendors to sell you more products. The answer to that will ultimately depend on what purpose you see Microsoft 365 backups serving.
The fact is that the Microsoft 365 platform is built from the ground up with resilience and data-integrity in mind, so many of the traditional reasons for backups, such as protecting against data corruption or system failure, are simply no longer of concern.
In addition to that, Microsoft 365 has various features to protect against other forms of data loss, such as accidental deletions and malicious attacks (assuming of course that you have appropriate licensing). So why bother with a backup then?
In our years of experience at Grassroots IT supporting clients with Microsoft 365, there are still several scenarios where the native data recovery capabilities can fall short, and third-party Microsoft 365 backups will shine.
When you need to minimise Microsoft 365 licensing costs
For those clients looking to actively minimise their licensing costs by choosing a lower-end plan, third-party backup solutions can provide functionality that might otherwise be missing, such as the Litigation Hold feature found in the more complete plans. Litigation hold is an invaluable tool for eDiscovery and compliance purposes, essentially allowing you to indefinitely keep any emails or documents. In lower-end plans without this feature, deleted data will ultimately become unrecoverable after a set retention period, unless you have third-party Microsoft Office 365 backups in place.
Another related scenario that we often face with cost-conscious clients is what to do with staff members’ Microsoft 365 data when they leave the organisation. To keep their profile fully active would require a paid license, while to archive their mailbox into a free shared mailbox would only retain their mailbox, and not data stored elsewhere, such as in OneDrive. With a third-party backup solution in place, the ex-staff member’s account can be fully deleted, safe in the knowledge that all their Microsoft 365 data has been retained within the backups.
When you need a point-in-time snapshot of your data
While the native Microsoft 365 backups do retain previous versions of your files to allow recovery from unwanted deletions, they can only go back so far, and don’t always allow you to restore from a particular point in time very easily. External backups on the other hand, provide you with the flexibility to restore from any point in time that has been captured within your backup schedule.
When you have compliance obligations to meet
For organisations subject to strict compliance regulations, such as those in healthcare or finance industries, having an additional layer of control over your Microsoft 365 data is non-negotiable. Microsoft 365 backups are also important for organisations looking to improve their cybersecurity posture by aligning with one of the major frameworks, such as the Essential Eight.
When data is intentionally deleted
It’s a scenario we all hope to never encounter, but the reality is that data can be intentionally deleted by disgruntled employees or external attackers. While Microsoft 365 does have a feature to recover recently deleted items, this only works if the data is still within the retention period and hasn’t been permanently deleted. Third-party backups are an essential safeguard against these types of malicious actions, ensuring that your organisation’s critical data remains safe and accessible.
When quick & complete data recovery is a priority
As capable as the native data recovery features of Microsoft 365 are, they don’t always make it easy to rapidly restore the data that you need, nor to recover the full structure of data, such as email folder structure or SharePoint document libraries. With third-party backups, you have the peace of mind that you can quickly and easily restore large quantities of data without any hassle.
Conclusion
Ultimately the decision is yours – are Microsoft 365 backups a necessity or overkill? From our perspective we see the addition of a third-party backup solution to your Microsoft 365 tenant as a wise investment. In some cases, it can provide the belt to Microsoft 365’s braces, while in other cases, without external backups, you may truly be sod-out-of-luck.
If you would like to talk about backing up your Microsoft Office 365 data, contact us today.
In today’s rapidly digitizing world, artificial intelligence (AI) has become synonymous with innovation. However, knowing how to introduce AI to your business can be a daunting prospect. Thankfully (and contrary to popular belief), integrating AI into your processes does not need to involve sophisticated systems or complex coding.
In fact, there are numerous simple AI integrations that can be readily incorporated into your existing business processes to streamline and automate your business operations. With AI, you can enhance efficiency, reduce errors, improve customer service, and ultimately drive growth.
Read on for some easy and accessible ideas to kick-start your AI journey.
ChatGPT - the one that started it all
If you haven’t already played around with ChatGPT, it’s a great place to start familiarising yourself with what Generative AI is capable of. Best of all you can get started for free by heading over to https://chat.openai.com and creating a free account.
ChatGPT is essentially a chatbot, so once you’re logged on to your free account, don’t be shy. Go ahead and start asking it some questions. Here are some ideas to get you started:
- “What can I make for dinner tonight with 3 eggs and some pine nuts?”
- “Help me to write a concise and polite email to my client summarising why we can’t help with their project.”
- “Help me to create a strategy for improving team culture in a growing business.”
The more you play with ChatGPT the more ideas you’ll come up with, I guarantee it! Once you’ve got the hang of it, consider encouraging your staff to also have a play, and come up with ideas for how they could use it in their daily activities. At Grassroots IT our engineers regularly use ChatGPT to help write friendly and professional emails to our clients, which has made a noticeable difference to the effectiveness of our communication.
Once you’re comfortable with ChatGPT, here are some power tips to help level up your AI game:
- Consider paying to access ChatGPT-4. Not only is this version more advanced in its “thinking” than the free ChatGPT-3.5 version, but it has live access to the internet, allowing you to use prompts such as “Please summarise today’s top news stories regarding commercial real-estate”
- You can ask ChatGPT follow-up questions. So, for example once we have today’s top news stories, we could then ask “Please tell me more about article #1”
- Don’t be shy to tell ChatGPT how you would like it to present its results. For example “Please compare the pros & cons of Makita vs Ryobi power tools, formatted in a table. “
- The secret to great results is in the prompt that you give it. In fact the hottest job on the market right now is a “Prompt Engineer”! Try some more advanced prompting, such as “Pretend to be an experienced digital marketer and …” or “Provide step by step instructions on how to…” or “My business is focussed on highly educated consumers between 25-30 years old. Help me to….”
Intelligent process automation with Power Automate
Microsoft Power Automate is powerful tool in the Microsoft 365 platform that allows businesses to leverage AI’s capabilities for advanced process automation. As a cloud-based service, Power Automate provides an intuitive platform to create, manage, and customize workflows that automate repetitive tasks.
The real strength of Power Automate lies in its AI Builder, a no-code AI capability that enables you to infuse artificial intelligence into your workflows. With AI Builder, you can automate tasks such as form processing, prediction modelling, text classification, and more.
For example, if your business deals with a high volume of invoices, you could use Power Automate with AI Builder to create a process that automatically captures and processes data from these invoices, significantly reducing manual data entry. Or, in a customer service context, AI Builder can be used to create a workflow that automatically triages incoming customer emails and directs them to the appropriate department, increasing efficiency and improving customer service response times.
Power Automate’s integration capabilities with a wide range of popular apps and services also means that your AI-powered workflows can connect seamlessly with the tools you use every day. Whether it’s saving attachments from Outlook emails to OneDrive, creating tasks in Microsoft Teams based on flagged emails, or syncing data with non-Microsoft platforms, Power Automate allows you to create holistic automated processes that streamline your business operations.
Level up your meetings with Otter
If you’re anything like me, it sometimes feels like you spend half your working day bouncing from one meeting to the next, leaving no time to gather your thoughts, review your notes and work out who needs to do what next!
This is where Otter.ai steps in as your handy AI meeting assistant. Otter uses AI-powered speech recognition technology to automatically transcribe and organize meeting notes in real-time, so you don’t have to. You can even import your existing calendar appointments and let Otter join the meeting for you, taking care of all the notetaking while you focus on actively participating in the discussion.
With its ability to identify different speakers and tag sections of the conversation, Otter makes it easy to quickly find specific information within your notes. And with its collaboration features, you can easily share and collaborate on your meeting notes with colleagues, making sure everyone is on the same page.
Conclusion
The important thing to understand about AI is that using it to streamline business operations is now table-stakes. Even if you’re not using AI yet, rest assured that your competition is. The good news is that integrating AI into your business can be surprisingly quick and easy. I encourage you to explore some of the ideas shared above, and if Grassroots IT can be of any assistance, contact us today.
As businesses increasingly migrate to digital platforms, cybersecurity has become a non-negotiable priority. Microsoft 365 leads the way in providing robust security solutions and offers an abundance of features designed to safeguard your business data and systems – but how do you navigate the plethora of options available to ensure that you’re choosing the best security measures for your specific needs without feeling overwhelmed? Enter Microsoft Secure Score.
Just as the name suggests, Microsoft Secure Score is a built-in tool that not only scores your security posture but also recommends actions for improvement. With Secure Score, enhancing your cybersecurity is no longer a daunting task but a series of quick, actionable wins that will strengthen your defence line further against potential threats.
What is Microsoft Secure Score?
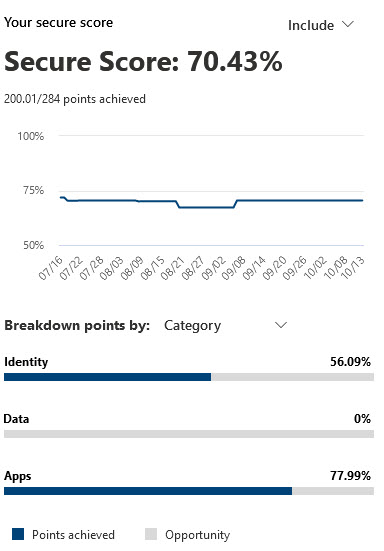
Secure Score is a free tool that comes with Microsoft 365 that analyses your organization’s security stance based on your unique use of Microsoft 365 services. It provides a numerical score, along with a detailed breakdown, of how well you are implementing the recommended security controls. Quite simply, the higher your Secure Score, the lower your risk level.
Secure Score monitors Identity, Apps, Data, and Devices in Microsoft 365, helping you to report on the current state of your security posture, suggest improvements by providing guidance, visibility and control, and compare yourself against similar sized organisations.
Importantly, it does not simply focus on one specific area of security in your Office 365 environment. Instead, it looks at all products available under your current licensing and providing recommended actions across multiple areas. Recommendations are presented in an easy-to-understand dashboard, grouped by product, and sorted by the impact the recommended change will have on improving the security of your Microsoft 365 environment. This approach makes it easy to focus your efforts in the right area and avoid spending unnecessary time on actions that won’t move the needle as much.
Key features of Secure Score
Key features of include:
Security Recommendations
Secure Score provides actionable security recommendations tailored to an organization’s specific environment. These recommendations cover areas like identity and access management, data protection, threat detection, and more.
Point-Based Scoring
Each recommended security improvement comes with a point value. By implementing the recommendations, your organization can earn points and increase your Score.
Comparison and Benchmarking
Secure Score allows you to compare your security posture with industry benchmarks and similar organizations. This feature provides valuable insights into how well you are performing relative to your peers.
Threat Intelligence Integration
The tool integrates with Microsoft Threat Protection, offering real-time threat intelligence and helping you stay ahead of emerging threats.
Historical Tracking
The system maintains a historical record of progress, enabling you to visualize your security journey and measure improvements over time.
Why use Microsoft Secure Score?
Microsoft Secure Score provides high impact recommendations to improve your cybersecurity posture, usually requiring little or no additional expense. Rather than requiring new and additional security services, Secure Score simply helps you to make the most of the features that you already have access to within the Microsoft 365 platform.
Importantly, Secure Score may help you reduce your cyber-insurance premiums. With cyber-insurance becoming a vital piece of any cybersecurity strategy, many insurers are now recognising the value of Microsoft Secure Score and factoring it in when calculating insurance premiums. Improve your Secure Score and you can potentially reduce your cyber-insurance premiums.
Not only that, but if your organisation aligns with one of the recognised cybersecurity frameworks, such as the Essential Eight, improving your Secure Score can also positively impact your alignment with your chosen framework.
Using Microsoft Secure Score
You can find your Secure Score in the Microsoft Defender Portal. Navigating the portal is quite intuitive, allowing you to focus on the insights and recommendations provided. Importantly, each recommended action also provides details on how the action will impact your security standing, along with any potential user impact.
Recommendations may range from reviewing an existing policy to implementing changes that may have a significant impact on users completing everyday tasks. As with all such changes, it’s important that you carefully assess the recommendation and consider the potential impact on operations.
Reporting and Tracking with Secure Score
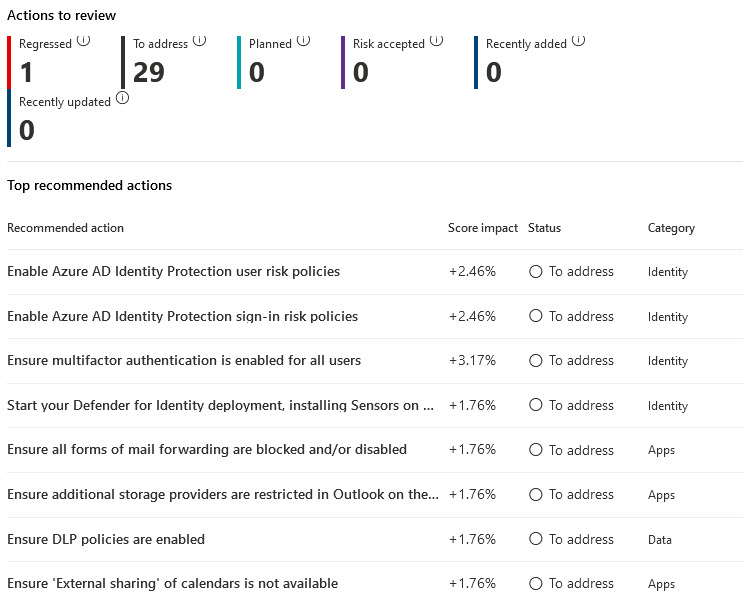
When embarking on a process of change, it’s important to measure and demonstrate progress over time. Thankfully the Secure Score portal provides a historical view of your organisations score over the last 90 days, showing a trend line that makes sudden changes easily visible. A list of recommended actions is also shown, showing when there was a change to each action, if points were gained or lost and allowing you to understand sudden changes in score.
The Secure Score dashboard shows different metrics and trends, where an action may have regressed, recent decreases, points achieved, along with a comparison against similar sized organisations. Metrics and trends can be shown over 7, 30, & 90 days or using a custom date range and can be filtered based on the 4 main categories Secure Score applies against.
Safely Implementing Changes (without the drama)
Unfortunately, there are too many stories of (easily avoided) problems being created when security changes are made without proper consideration. One story that we’ve heard too many times is when an over-enthusiastic sysadmin has enabled multi-factor authentication or conditional access policies within Microsoft 365 without properly preparing the organisation – thus effectively locking many, if not all, staff out of the system. Problems like this are easily avoided though, with appropriate forethought and planning.
For many clients we find that an effective approach is to develop a roadmap of changes based on the Secure Score recommendations, and then progressively work through these changes over a period of weeks, reviewing improvements in their Secure Score as they go. Some changes may be quick and easy to implement, while others may require more careful management, such as technical change control and user training. By approaching this as a progressive roadmap of smaller actions you can ensure ongoing improvement while managing the risk of disruption.
How we improved both user experience and security with secure score
Grassroots IT recently helped a mid-sized non-profit organisation that was struggling with their systems. They reported inconsistent user experience across their Tenant, no defined settings for users when accessing systems and their users didn’t trust that they could easily access Office 365. When a review was conducted of the organisation’s Secure Score, it was immediately apparent that there were problems with both Identity and Apps within their tenant.
Utilising the recommended actions in Secure Score, Grassroots IT was able to implement multiple changes to their environment that made the user experience easier while also improving their overall security posture. Some of these changes included simplifying the user login process, enabling self-serve password recovery and using a single authentication service for apps. At the same time, multifactor authentication was enabled for all users, and appropriate policies were implemented to protect users from malicious content and emails, significantly improving their Secure Score and security posture.
Additional Resources
Microsoft Secure Score is a powerful tool for improving the security of your Microsoft 365 environment. To learn more, speak to us today, or explore some of these additional resources.
Key Signs You Need a New Managed Service Provider
Change can be hard, especially when it comes time to move on from a relationship that no longer serves your needs. Change can be even harder when that relationship is with your IT partner or Managed Service Provider. With IT at the heart of modern business, you need a strong relationship with the right MSP. With a robust partnership with your Managed Service Provider (MSP) can enhance efficiency, improve security, reduce costs, and most importantly, ensure your business stays ahead in today’s rapidly evolving technology landscape.
Of course, what this means will be different for each of us and may change over time, but the important thing is to recognise if your existing MSP relationship is no longer working for you, and when it’s time to move on. Over the years at Grassroots IT, we’ve helped numerous companies move on from their incumbent IT partner once they realised that they deserved more from the relationship, so we have a pretty good idea of what the most common areas are where MSP’s fail to perform.
Have you lost confidence in your Managed Service Provider?
The number one sign that it’s time to find a new MSP is that you have lost confidence in them. This may sound obvious, but sometimes the hard part can be recognising the situation for what it is.
So how do you recognise when you’ve lost confidence in your MSP? Here are some common behaviours that may indicate it’s time to rethink your IT relationship.
- You dread having to call them for anything.
- Issues are never resolved properly the first time.
- You always want a second opinion on their advice.
- Reported issues disappear into a black hole.
If these statements resonate with you, it’s crucial to address the situation and seek change. Remember, you deserve an MSP that instils confidence, provides effective solutions, and whose advice you can trust.
Do issues never seem to be solved properly?
Another important sign that your relationship with your Managed Service Provider isn’t working is when you consistently experience recurring issues that never seem to be resolved correctly. No matter how many times you report the issue it’s always treated as if it’s the first time it’s happened, or if it is acknowledged as recurring, a proper root-cause analysis and resolution never seems to be a priority.
These technical glitches keep resurfacing time and again, causing disruptions to your business operations and leading to unnecessary stress and frustration. This persistent problem can not only indicate a lack of expertise or commitment on the part of your MSP but also highlights the urgent need to consider partnering with a more capable and reliable MSP who can provide the necessary support and solutions to address your unique business needs effectively.
Making the switch to an MSP that is dedicated to delivering top-notch services and expertise can help ensure that your technology infrastructure runs smoothly, enabling you to focus on growing your business without unnecessary hindrances.
Is your MSP helping to move you forward?
A significant red flag to watch for is if your MSP lacks a proactive, forward-thinking approach. The technology landscape is continually evolving, and your MSP should not only be keeping up with the pace but also staying one step ahead. They need to be actively speaking to you about potential weaknesses and risks in your IT infrastructure and suggesting improvements and updates to optimise your systems.
An MSP should not merely be reactive, responding only when issues arise. Instead, they should be consistently strategising and planning for the future, ensuring your business is equipped with the most up-to-date and efficient technology solutions. If your MSP is failing to communicate and engage with you in planning and updating your IT systems proactively, it might be time to consider a transition.
Your business deserves a partner who values progression and innovation, effectively guiding you through the ever-changing maze of technology to enhance your operational efficiency and growth.
Do you struggle with their poor communication?
The relationship between you and your MSP is a crucial one. But if communication or responsiveness is lacking, this can derail the success of your IT partnership. You should expect timely responses from your MSP at every step along the way and a reliable cadence of proactive communication, such as quarterly reviews. If they fall short in this area, it could be an indication that their service standards are not meeting your expectations, indicating that it’s time to consider making a switch.
When looking for an MSP with whom you can build a strong and mutually beneficial relationship, search for someone who prioritizes communication and values customer service. Look for an MSP that is easy to talk to, responsive when you reach out to them, clearly communicates how they plan to address any issues, and keeps you in the loop throughout the process.
Do your MSP’s values align with yours?
The right MSP should be a good fit for your company culture. You and your MSP must share similar values and beliefs, as this will ensure that you feel comfortable working with each other and can collaborate effectively.
At Grassroots IT our core values are fundamental to how we do business, influencing everything from how we select our team members to which clients we choose to work with.
When you find the right MSP, it can be an incredibly rewarding relationship that helps to propel your business forward. So, make sure you take the time to do your research and find someone who understands your goals and values, applies their expertise in a way that aligns with your vision and expectations.
When to Consider Switching Your Managed Service Provider
Selecting the right Managed Service Provider is a crucial decision that significantly influences your business’ growth and success. It’s essential to recognise the red flags when they arise and make the necessary changes to ensure that your IT partnership is solid, effective, and forward-thinking.
Consider the points highlighted above and evaluate whether your current MSP relationship is empowering or hindering your business. Remember, you deserve an MSP that is not just a service provider, but a partner who understands your business, aligns with your culture, and is dedicated to helping you navigate through the technology landscape.
Recognise when it’s time to switch and take the step, even if it seems daunting. The right MSP can truly transform your business, and the journey towards that beneficial relationship is worth the effort.
In a post-pandemic world, flexible working arrangements have become the norm for many. Where working remotely was previously the exclusive domain of salespeople and on-site consultants, these days an office full of staff seems a rare sight, with online meetings commonplace.
While the long-term future of work is still unclear, it’s fair to say that remote working in some form is here to stay, bringing with it new challenges for business leaders, not least of all those tasked with cybersecurity. Old approaches to securing the organisations digital assets have been rendered outdated, while new unforeseen risks have emerged almost overnight.
So, what are the most pressing cybersecurity risks with a remote workforce, and how do you ensure the ongoing protection of your business in light of these changing threats?
Understanding the risks
The various tools and techniques that cyber criminals employ to attack those working from home are generally no different to those used elsewhere, however in a work-from-home context some threats are greater than others and can pose unique challenges. Here are three of the highest risk cyber-threats for staff working from home.
Phishing & other scams
Phishing and other such scams are fraudulent attempts to obtain sensitive information from users, such as usernames, passwords and credit card details, usually by sending fake email purporting to be from a known, trusted person or brand. WFH users are often more vulnerable to such attacks as they may not have the same level of active awareness as others, may use personal email accounts alongside work email, and may not have ready access to corporate security tools and support.
Read more: How to identify a phishing email
Device security
Device security refers to the protection of physical computing devices, such as laptops, smartphones and tablets against unauthorised access which would in turn give cybercriminals access to confidential corporate information. This is of particular concern with staff working from home as physical security of devices is likely to be less than in an office environment, particularly when others have access to the same work environment at home.
Home workers are also more likely to use personal computing devices rather than business supplied devices, with or without explicit permission to do so. Personal devices are likely not configured with the same security controls as company-owned devices, nor actively monitored, managed or updated with the latest security updates.
Data leakage
Data leakage is the unauthorised transmission of data from within the company to an external destination or recipient, whether intentionally or otherwise. Users working from home are likely to use a poorly secured home network, have inadequate access controls in place around confidential information, and may even use personal cloud services instead of, or alongside approved company services, all of which pose the very real risk of leaking important company information.
Implementing Solutions
The good news is that there are proven strategies for effectively mitigating each of these threats in a work-from-home scenario.
Cloud Platforms
Cloud platforms such as Microsoft 365 are by nature designed to support remote working. It doesn’t matter whether you are physically in the office, at home or on a client site, the way you access a cloud service, and the security controls available are the same. By their very nature this makes cloud platforms a better, and potentially more secure option for supporting home-based workers than traditional infrastructure solutions.
Device Management
Ensuring the security of physical devices at home presents a unique challenge best addressed by strong policy. A work-from-home policy must enforce the use of company-owned devices only, enabling the deployment of strong security controls to the device such as patch management, managed detection & response agents and data encryption. The policy must also discuss the physical security of devices, the use of automatic screen locking and immediate mandatory reporting if a device is misplaced.
It is worth briefly mentioning the topic of Bring-you-own-device (BYOD), whereby staff may use their own devices to access corporate systems. Allowing for BYOD is a perfectly valid option, however, please be aware of the security implications of such a policy and adjust accordingly.
Employee training
A strong culture of cybersecurity awareness can be one of your most effective defences against security breach and data loss, and especially so when staff work from home. Users must be well versed on recognising threats such as phishing emails and how they should respond. They should also be clear on all relevant policies and understand the importance of compliance.
Read more: Building a culture of cybersecurity awareness in your business.
Conclusion
The post-pandemic work-from-home movement is here to stay, with undeniable benefits for many people. It does however bring with it unique cybersecurity risks that the organisation must proactively address to avoid inadvertently allowing cyber criminals access to corporate systems.
Grassroots IT is well versed in helping our clients support their home-based workers with secure, scalable systems. For help protecting your remote workers contact us today.
Explore Common Cybersecurity Myths and Misconceptions
In the digital age, cybersecurity has become a critical concern for businesses of all sizes. However, there are numerous misconceptions surrounding this complex field that can lead to complacency and, ultimately, vulnerability. In this post, we debunk ten of the most common cybersecurity myths that could be putting your business at risk.
Myth 1: My business is too small/boring to be attractive to hackers
Every business, regardless of its size or industry, is a potential target for cybercriminals. Small businesses often fall into the trap of believing they’re too insignificant to attract attention. However, hackers often target smaller businesses precisely because they tend to have weaker security measures in place. With many cyber-attacks launched at scale (eg: phishing emails) the incremental cost to hackers of targeting your small, boring business is negligible, yet the potential pay-off can still be significant.
Myth 2: My data is safe in the cloud
While cloud storage providers implement robust security measures, it doesn’t mean your data is invincible. Cybercriminals have been known to breach cloud security, and human errors can also lead to data exposure. It’s crucial to understand the shared responsibility model of cloud security and ensure you’re doing your part to protect your data. The cloud providers provide the platform, and the means to secure your data, but ultimately the responsibility for doing so is yours.
Read more: 5 Critical Questions to Ask About Your Microsoft 365 Security
Myth 3: My data is safe on my own server
Storing data on your own server doesn’t automatically make it safe. Without proper security measures in place, your server can be just as vulnerable as any cloud service. Regular updates, patches, and strong access controls are essential to protect your data (many of which are automatically done for you in the cloud).
Myth 4: Cybersecurity is my MSPs responsibility
While your IT department or MSP plays a crucial role in implementing and maintaining security measures, cybersecurity is everyone’s responsibility from the bottom of the org chart all the way to the board. A commitment to cybersecurity must be lead from the top, with company directors and CEOs holding particular responsibilities for protecting the organization’s digital assets.
Read more: 5 questions board members need to ask about cybersecurity
Myth 5: My team works from home, so security is their responsibility
Remote work has blurred the lines of responsibility for cybersecurity. However, as an employer, it’s your duty to provide secure systems and training to your employees. This includes secure communication tools like Microsoft Teams, and guidelines on safe online practices.
Myth 6: Cybersecurity is too expensive
With the average cost of a data breach in Australia reaching $4.4 million, the cost of a data breach can far outweigh the investment in cybersecurity. While implementing robust security measures may require an upfront investment, this can be far less costly than the potential financial and reputational damage caused by a breach.
Myth 7: I’ll know if my systems have been hacked
Many breaches go undetected for months, or even years. Cybercriminals often aim to infiltrate systems without detection, stealing data or causing damage over time. Regular system audits and monitoring are essential to detect and respond to breaches promptly.
Learn more: 24×7 peace of mind with managed detection & response
Myth 8: My staff are too smart to get hacked
Even the smartest individuals can fall victim to sophisticated cyberattacks. Phishing attacks, in particular, have become increasingly convincing and can easily trick unsuspecting users. Regular training and cybersecurity awareness are crucial to equip your staff with the knowledge to identify and avoid such threats.
Read more: Building a culture of cybersecurity awareness in your business
Myth 9: Strong passwords are enough
While strong passwords are a fundamental part of cybersecurity, they’re not a panacea. Multi-factor authentication (MFA), secure network connections, and regular software updates are just as important in protecting your systems.
Myth 10: We only need to protect against external hackers
Insider threats, whether malicious or accidental, are a significant risk. Employees can inadvertently cause a breach by clicking on a malicious link or misconfiguring a database. Regular training, strict access controls, and monitoring can help mitigate this risk.
Dispel Cybersecurity Myths To Protect Your Business!
Cybersecurity is a complex field that requires a proactive and informed approach. In the realm of cybersecurity, complacency can be your biggest enemy. Grassroots IT are cybersecurity experts, ready to help secure your business against cyber criminals. To see how we can help, speak with us today.
Microsoft Office 365 is built from the ground up to be a highly secure platform, but that doesn’t necessarily mean that your own Office 365 environment is configured securely. There are numerous different ways that organisations can use Office 365, and just as many ways that it can be configured.
Ultimately the responsibility for securing your Office 365 environment, and the information and data stored in there, rests with you. Microsoft provides the platform and the means, but it’s up to you to consider your unique situation and ensure that appropriate security measures are taken.
So how do you know if your Office 365 environment is secure? Every organisation is different, and with so many ways of using and securing Office 365 there is no one-size-fits-all solution. The good news is that there are some well-established best-practices that can significantly strengthen the security of your environment.
Here are five critical questions that you need to ask about your Office 365 security to ensure that you’re properly protected.
#1. What Microsoft Office 365 plan do we use?
Let me start by saying that Microsoft has a frustrating habit of changing product names and bundles regularly, which can lead to some confusion. So, for the sake of clarity, let me share a bit of history with you.
First there were the Office 365 plans, offering a suite of products such as Word, Excel, Email and Teams. Then Microsoft added a whole new line of plans called Microsoft 365, which included all the things from Office 365, plus added a whole lot more, mainly to do with security and governance. Then more recently the Office 365 name has been retired entirely, leaving only Microsoft 365 plans to choose from. If you were using Office 365 plans before these changes happened, you will still be on those same Office 365 plans now.
It’s important to understand which Microsoft Office 365 plan you subscribe to, because not all of them have access to the better security features. For most organisations, we recommend that you subscribe to the Microsoft 365 Business Premium plan, or for some larger organisations, the enterprise level Microsoft 365 E3 or Microsoft 365 E5 plans. The important services that are included in these plans (but not the lower plans) are Azure Information Protection and Intune, both of which bring a range of security and data governance capabilities to your environment.
Recommendation
Review all your Microsoft Office 365 subscriptions and consider upgrading any that are not Microsoft 365 Business Premium, E3 or E5 so that you can take advantage of the better security and governance capabilities.
#2. What’s our Microsoft Secure Score?
Microsoft Secure Score is a rating of your organisation’s Microsoft 365 security posture, compiled from a range of configurations, metrics and various other data points, depending on what Microsoft 365 plan you subscribe to, and what services you use. The higher the number, the more secure you are.
In addition to a numeric score, the Secure Score dashboard will also provide actionable insights and prioritized recommendations tailored to your unique needs. By following these recommendations, you can progressively improve your Secure Score and strengthen the security posture of your Microsoft 365 environment to provide better protection for your confidential data.
Recommendation
Review your Secure Score and progressively implement the recommendations to improve your score.
#3. Is Multi-factor Authentication enabled on all our Microsoft 365 accounts?
Multi-factor authentication (MFA) is an authentication method that requires a user to provide two or more verification factors to prove their identity and gain access to your Microsoft 365 environment, most often a password plus a unique code provided by a separate app.
Despite being one of the most effective cybersecurity measures you can implement in your Microsoft 365 environment, MFA is not always enabled by default or enforced across all accounts. The important point to remember is that your security is only as strong as the weakest link, so for MFA to be most effective it must be enforced on all accounts in your Microsoft 365 environment, not only some of them.
Recommendation
Review all accounts in your Microsoft 365 environment and enable MFA where necessary. Configure Microsoft 365 to enforce MFA on all accounts by default.
Read more: 3 reasons you need to enable Multi-factor Authentication (MFA) today
#4. Are we using dedicated Microsoft 365 admin user accounts?
Every Microsoft 365 environment has one or more “admin” user accounts. These accounts possess elevated privileges that allow them to perform sensitive tasks such as changing system settings and accessing data anywhere across the environment. These admin privileges can be seen as the “keys to the kingdom”, and if allowed to fall into the wrong hands can be exploited to cause significant damage.
User accounts used for everyday tasks such as checking email and editing work documents should never be granted such elevated admin privileges, so as to reduce any potential harm should the account be compromised. Instead, dedicated “admin” accounts should only ever be used for duties requiring elevated security privileges.
Not only does this approach reduce the risk of accidental changes or security breaches, but it also makes it easier to monitor and audit their activities, improving accountability and traceability of any suspicious actions taken within your Microsoft 365 environment.
Recommendation
Review all user accounts in your Microsoft 365 environment for elevated admin privileges and remove such privileges in favor of dedicated admin accounts.
#5. How are we monitoring for suspicious activity within Microsoft 365?
Even with a well secured Microsoft 365 environment, ongoing monitoring and alerting of unusual activity is important for the prevention of a full-blown security incident. Monitoring can help identify a range of suspicious activities, such as multiple failed login attempts, unusual data access or transfers, and changes in user permissions. These could be signs of a brute force attack, data breach, or insider threat.
Moreover, monitoring isn’t just about detection, it’s also about response. When you spot suspicious activity, you can quickly investigate, take corrective action, and learn from the incident to strengthen your defenses.
Recommendation
Ensure monitoring is configured within your Microsoft 365 environment, and alerts are sent to the most appropriate person to take action as required.
Microsoft 365 is a highly secure platform, but that doesn’t mean that your organisation’s Microsoft 365 environment is secure by default. Microsoft provides the means, but ultimately, it’s up to you to ensure that your environment is secured appropriately, and that starts with asking the right questions.
If you have questions about your Microsoft 365 security, Grassroots IT can help. Speak with us today.
What is Cybersecurity Awareness?
Cybersecurity awareness is the level of understanding and mindfulness that people in your organisation have of the various cybersecurity threats that they may face, and how they should best respond.
A shocking 82% of all data breaches involve some human element, such as social engineering or through plain old human error and misuse. What this tells us is that people – our staff, suppliers and partners – can not only be the weakest link in our cybersecurity posture, but also offer the greatest potential to help protect against cyberattack.
Cybersecurity awareness is the lever that we must use to shift our people from being our biggest cyber-risk to being our strongest line of defence.
Why is Cybersecurity Awareness important?
With the average cost of a data breach in Australia reaching $4.4 million, cybersecurity attacks pose a very real and present threat to organisations of all types. Cybersecurity frameworks such as the ACSC Essential Eight and the NIST CSF can help us with strategies and security controls to help mitigate these risks, but technical controls can only help so far.
With the statistics clearly showing that the human element plays a major role in the effectiveness of our defences, we ignore cybersecurity awareness at our peril.
How to build a culture of cybersecurity awareness
Intentionally building any culture takes time, commitment and consistency to create and reinforce the behaviours that we wish to see in our organisation. Building a culture of cybersecurity awareness is no different.
Here are five practical ways to engage your organisation and build the cyber-aware culture you need.
Secure leadership buy-in
Culture is lead from the top and cybersecurity awareness is no different. All organisations look to their leaders to set the direction for the company not only through explicit statements, but also through implicit and implied messaging. Leaders must be seen to embrace the importance of a cybersecurity aware culture, and to lead by example.
Securing leadership buy-in can be helped by:
- Taking a holistic view of the organisation, of which a cybersecure culture is merely one piece.
- Connecting a cyber-aware culture to the company’s strategy, goals and aspirations.
- Clearly communicating the business case for strong cybersecurity awareness.
Promote robust policies, procedures and best practices
Robust cybersecurity policies and procedures are at the heart of any cyber-secure organisation. Policies and procedures must walk the fine line between protecting the organisation and being overly restrictive on how staff may go about their work. Too lenient and they may be ineffective – too stringent and staff satisfaction and productivity may suffer.
Policies and procedures should be promoted regularly to keep them top of mind with staff, along with examples of best practice responses to various likely scenarios.
Some common ways of promoting cybersecurity policies and best practices can include:
- Ensure policies and procedures are clear, actionable and easily accessible to all staff.
- Download, print and share posters and resources promoting cybersecurity best practice.
- Communicate examples of real-world cybersecurity threats, and best practice responses through internal communications channels.
Conduct regular cybersecurity training
Regular cybersecurity training will not only keep cybersecurity top of mind and reinforce best-practice threat response, but it will provide an avenue for keeping staff updated on the latest cyber-threats they may face. The challenge of course is to keep training engaging and effective.
You might like to consider these Ideas for delivering engaging cybersecurity awareness training:
- Mix up the format of delivery between online, in-person and self-paced.
- Keep training sessions short, high energy and with a clear take-away message.
- Consider bringing in an external trainer to inject new ideas and energy.
Schedule simulated cyberattacks
Research has shown simulation-based cybersecurity awareness training to be the most effective when compared to other methods such as instructor led (a close second place) and online delivery. Simulations may be run periodically to quantify the level of cybersecurity awareness in the organisation and identify improvement over time.
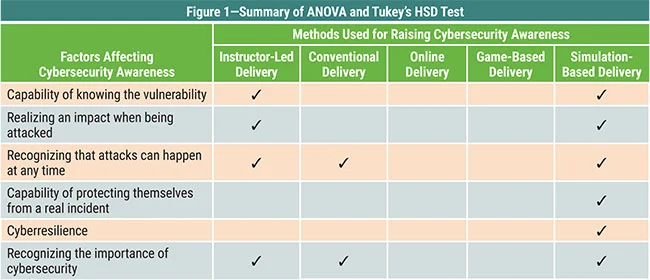
Table courtesy of ISACA.orgIn practice, the most common form of simulated cyberattack is referred to as “Friendly Phishing”, whereby staff are sent a fake phishing email to see how they respond. Those who are successfully tricked by the fake phishing email are immediately shown the error of their ways and are offered a brief online training snippet to educate them on how they could have identified the threat in time, and what a more appropriate response would have been.
Be consistent and stay informed
When impacting any organisational change, it is important to be consistent both in the message and the delivery. Be clear up front what you want your cybersecurity culture to look like and ensure that all key stakeholders are aligned and have the tools available to drive the necessary change.
Organisational culture requires ongoing stewardship. It takes time to establish the culture that you want, and ongoing vigilance to keep it strong. Maintaining an effective culture of cybersecurity awareness is an ongoing process, not a once-off activity
Conclusion
Cybersecurity awareness presents both the biggest threat and the largest opportunity to your organisation’s cybersecurity posture. A poor level of awareness will leave you exposed to attack, regardless of what technical security measures you may have in place. A culture of high cybersecurity awareness on the other hand will be your strongest line of defence in protecting your company.


