More and more Australian organisations are discovering the strategic advantage of ISO 27001 certification. It’s exciting to see businesses of all sizes embracing this globally recognised security standard, opening doors to new partnerships and market opportunities. What was traditionally the domain of enterprise organisations has evolved into a powerful business enabler for growing companies across the country.
What’s ISO 27001 All About?
Strip away the fancy language, and ISO 27001 is simply an internationally recognised way to prove you’re serious about protecting information. While it might sound complex, at its heart it’s about having a systematic approach to keeping customer data safe, protecting your business from cyber threats, managing access to information, and being prepared when things go wrong. Think of it like a driver’s licence for information security – it proves you know what you’re doing and can be trusted to handle sensitive information properly.
Meeting ISO Requirements with Microsoft 365
The good news is that Microsoft 365 already includes a range of features that can directly support your journey to ISO 27001 compliance. Let’s look at exactly how you can use Microsoft 365 features to meet specific ISO requirements. Here’s your practical guide to ticking those ISO boxes using tools you already have.
User Access Management
What ISO Requires
The standard demands formal processes for managing user access throughout the entire employee lifecycle. This control exists because inappropriate access rights are a major security risk – think ex-employees with active accounts, or staff with more system access than they need. ISO wants to see that you’re actively managing these risks through formal processes and regular reviews. You need a systematic way to grant, modify, and revoke access based on people’s roles, ensuring everyone has exactly what they need to do their job – nothing more, nothing less.
Real-world example
- When Sarah from Accounts leaves, all her access needs to be removed within 24 hours
- When Jim moves from Support to Sales, his system access needs to change to match his new role
- Every quarter, managers need to confirm their team members still need their current access levels
- When Dave from IT needs admin access to fix an urgent issue, it should be time-limited and logged
How to Meet It with Microsoft 365
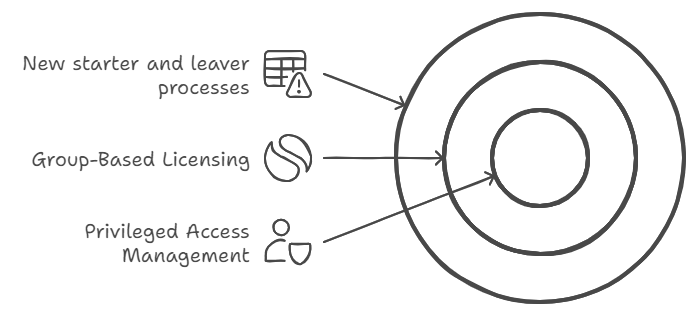
1. For new starter and leaver processes:
- Set up automated workflows in Azure AD: When HR marks an employee as terminated, their accounts are automatically disabled
- Configure group-based licensing: New sales staff automatically get Salesforce access, while marketing gets Adobe Creative Suite
- Use access reviews: Managers get quarterly emails to verify their reports still need access to sensitive data
- Enable Microsoft Groups expiration: Teams/SharePoint access automatically expires if not renewed
2. For privileged access management:
- Set up just-in-time access: IT staff request admin rights for 2 hours to perform maintenance
- Configure approval workflows: Senior IT approval required for global admin access
- Enable session recording: All admin activities in sensitive systems are logged
Authentication Controls
What ISO Requires
You need to prove you’re properly controlling system access. This requirement recognises that passwords alone aren’t enough anymore. ISO wants evidence that you’re using modern authentication methods to verify users’ identities, especially when accessing sensitive information or systems. It’s about making sure that even if someone gets hold of a password, they can’t automatically access your systems. The standard also emphasises the importance of protecting access information – like making sure password rules are strong enough and that you can detect and block suspicious login attempts.
Real-world examples:
- Jane shouldn’t be able to log in with just a password when accessing payroll data from home
- Failed password attempts should lock an account after 5 tries
- If Bob’s session is idle for 15 minutes, he should be logged out
- When Alice tries to log in from an unusual location, extra verification should be required
How to Meet It with Microsoft 365
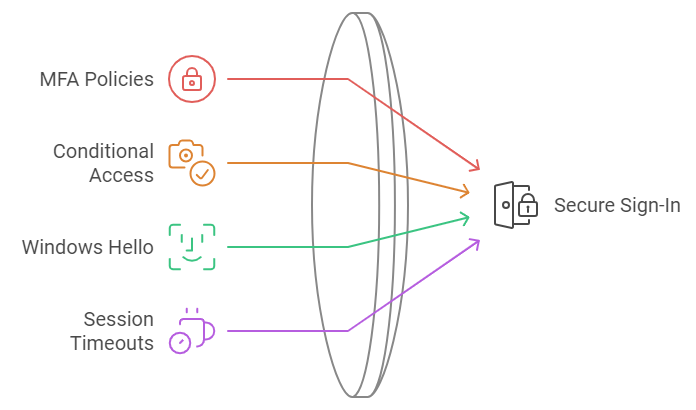
1. For secure sign-in:
- Configure MFA policies: Force additional verification for all remote access
- Set up Conditional Access: Require managed devices for accessing customer data
- Enable Windows Hello: Replace passwords with biometric login
- Configure session timeouts: Auto-logout after 15 minutes of inactivity
Information Classification
What ISO Requires
You must show that sensitive information is properly identified and protected. This control recognises that not all information needs the same level of protection – your marketing brochure doesn’t need the same security as your customer credit card details. ISO requires you to think through what types of information you handle, how sensitive each type is, and what protection it needs. Then you need to show that you’ve got systems in place to consistently identify and protect information based on its sensitivity level.
Real-world examples:
- Customer credit card details need the highest level of protection
- Internal project documents shouldn’t be shareable outside the company
- HR documents should only be accessible by the HR team
- Marketing materials can be widely shared but not modified by everyone
How to Meet It with Microsoft 365
1. For automatic classification:
- Create sensitivity labels: “Confidential-Finance”, “Internal-Only”, “Public”
- Configure auto-labelling: Documents with credit card numbers automatically marked as “Confidential”
- Set up visual markers: Confidential documents get a red header saying “Internal Use Only”
2. For information handling:
- Enable encryption: “Confidential” documents can only be opened by approved users
- Set up DLP: Block sharing of documents containing tax file numbers
- Configure SharePoint permissions: HR site only accessible by HR team members
Cryptographic Controls
What ISO Requires
Sensitive data must be properly encrypted. This requirement goes beyond just turning on encryption – ISO wants to see that you’ve thought through when and where encryption is needed, and that you’re managing it properly. This includes having formal policies about what needs to be encrypted, managing encryption keys securely, and making sure your encryption methods are strong enough for the sensitivity of the data you’re protecting. It’s about ensuring that if someone does get unauthorized access to your systems, they still can’t read your sensitive data.
Real-world examples:
- Client contracts must be encrypted when stored
- Financial reports being emailed to the board need encryption
- Mobile devices with company data must be encrypted
- Backup files need to be encrypted before going to cloud storage
How to Meet It with Microsoft 365
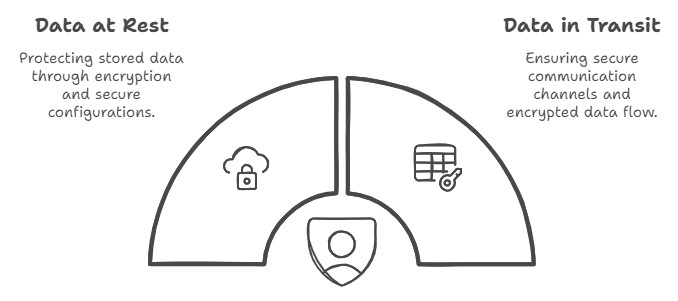
1. For data at rest:
- Enable BitLocker: All laptop drives automatically encrypted
- Configure SharePoint encryption: All documents encrypted with unique keys
- Set up Exchange mailbox encryption: Emails encrypted by default
2. For data in transit:
- Enable TLS: All email communications encrypted in transit
- Configure secure external sharing: Client portal access using encrypted connections
- Set up encrypted backup: Automatic encryption before cloud backup
Logging and Monitoring
What ISO Requires
ISO needs you to prove you’re actively monitoring your systems. This means having systems in place to detect, capture, and investigate security events and user activity. It’s not just about recording what happens – you need to show that you’re actively reviewing these records and can spot potential security incidents quickly. Think of it like CCTV for your IT systems – it needs to be recording, but someone also needs to be watching the monitors.
Real-world examples:
- All admin actions in key systems need to be logged and reviewable
- Failed login attempts need to be monitored and investigated
- File access patterns need to be tracked to spot unusual behaviour
- System changes need to be logged and attributable to specific users
How to Meet It with Microsoft 365
1. For audit logging:
- Enable Unified Audit Logging in Security & Compliance
- Configure alert policies for sensitive actions
- Set up log retention policies for compliance
2. For security monitoring:
- Enable Microsoft Defender for Cloud Apps
- Configure alert policies for suspicious activities
- Set up automated incident reporting
Communications Security
What ISO Requires
Information needs to be protected whenever it’s being shared or moved around. This control focuses on keeping data safe when it’s in transit between systems or being shared with external parties. It’s about making sure sensitive information can’t be intercepted or tampered with when it’s moving between point A and point B, whether that’s within your network or out to external partners.
Real-world examples:
- Customer data being shared with partners needs encryption
- Confidential emails need to be protected from interception
- File transfers between systems need to be secure
- External collaboration needs to be controlled and monitored
How to Meet It with Microsoft 365
1. For email security:
- Enable Exchange Online Protection
- Configure anti-phishing policies
- Set up Safe Attachments and Safe Links
2. For secure file sharing:
- Configure SharePoint sharing policies
- Enable Teams external access controls
- Set up secure guest access policies
The Bottom Line
Getting ISO 27001 certified doesn’t mean buying new security tools. Microsoft 365 includes powerful features that map directly to ISO requirements – you just need to know what to turn on and how to configure it.
Need help setting up these controls or mapping them to your ISO requirements? That’s what we do. Let’s talk about getting your Microsoft 365 environment ISO-ready.
For small to medium-sized businesses, Microsoft 365 Business Premium offers a robust suite of productivity tools coupled with advanced security features. However, many organisations are not taking full advantage of the security capabilities included in their subscription. In this post, we’ll explore the key security features of Microsoft 365 Business Premium and how you can leverage them to protect your business.
Understanding Microsoft 365 Business Premium
Microsoft 365 Business Premium is more than just a productivity suite—it’s a comprehensive solution that combines the familiar Office applications with advanced security and device management capabilities. This license tier is often considered the “sweet spot” for small to medium-sized businesses, offering enterprise-grade features at a fraction of the cost.
Key Security Features in Microsoft 365 Business Premium
Let’s dive into the security features that come standard with your Business Premium license:
1. Microsoft Defender for Office 365 (Plan 1)
Microsoft Defender for Office 365 is a cloud-based email filtering service that helps protect your organisation against advanced threats like phishing and zero-day malware.
Key components include:
- Safe Links: This feature provides time-of-click verification of URLs in emails and Office documents. It helps protect your organisation by checking web addresses against a list of known malicious links.
- Safe Attachments: This feature checks email attachments for malicious content. It opens attachments in a virtual environment to detect malicious behaviour before delivering the email.
- Anti-phishing protection: Advanced machine learning models and impersonation detection help protect your users from phishing attacks.
Pro Tip: These features aren’t necessarily enabled by default, so make sure to activate them to take full advantage of their capabilities.
2. Intune Mobile Device Management
Intune is Microsoft’s mobile device management (MDM) and mobile application management (MAM) platform. It allows you to manage both company-owned and personal devices used to access company data.
Key benefits include:
- Enforce device-level security policies (e.g., requiring a PIN to unlock the device)
- Selectively wipe company data from lost or stolen devices
- Manage and deploy apps to devices
Pro Tip: Start with basic policies like requiring a device PIN and the ability to remotely wipe company data. Gradually introduce more advanced policies as your team becomes comfortable with the system.
3. Azure Information Protection (AIP)
AIP helps you classify, label, and protect sensitive information. It can automatically detect sensitive data types (like credit card numbers or health information) and apply appropriate protections.
Key features:
- Prevent sensitive information from being shared inappropriately
- Track and control how protected information is used
Pro Tip: Begin by identifying your most sensitive data types and creating policies to protect them. Educate your users on the importance of data classification and how to use the AIP tools effectively.
4. Multi-Factor Authentication (MFA)
MFA is one of the most effective ways to protect against unauthorised access. It requires users to provide two or more verification factors to gain access to a resource, significantly reducing the risk of compromised accounts.
Pro Tip: Implement MFA for all users, starting with administrators and gradually rolling out to all staff. Consider using the Microsoft Authenticator app for a seamless user experience.
5. Conditional Access Policies
Conditional Access allows you to control access to your resources based on specific conditions. You can create policies that grant or restrict access based on factors like user location, device status, and detected risk level.
Key use cases:
- Block access from countries where your business doesn’t operate
- Require MFA for access to sensitive applications
- Ensure only managed and compliant devices can access company resources
Pro Tip: Start with a few critical policies and gradually expand. Always test new policies in a limited pilot before full deployment.
6. Exchange Online Archiving
While primarily a compliance feature, Exchange Online Archiving contributes to security by helping you retain and protect important email data. It provides users with an archive mailbox for storing old email messages.
Key benefits:
- Automatic movement of old emails to the archive based on policies
- eDiscovery capabilities for legal or compliance needs
- Retention policies to ensure important data isn’t accidentally deleted
Pro Tip: Set up retention policies that align with your industry regulations and business needs. Train users on how to access and use their archive mailboxes effectively.
Case Study: Small Business Success with M365 Business Premium Security
One of our clients, a local mining company with 70 employees was struggling with security concerns, particularly around protecting client financial data. By implementing Microsoft 365 Business Premium and fully leveraging its robust security features, the company saw significant improvements:
- 90% reduction in phishing emails reaching user inboxes
- Zero data breaches in the 6 months following implementation
- Improved ability to meet industry compliance requirements
- Increased employee productivity due to reduced downtime from security incidents
- Streamlined device management using Intune Compliance and configuration policies
- Standardised app deployment to all users leveraging Intune app deployment policies.
- Improved access controls using Conditional Access policies to for Geo Location, User risk and MFA
The firm faced initial challenges with user adoption, particularly around MFA and Geo Location policies. However, with a comprehensive user training campaign, they achieved full adoption within three months.
Conclusion
Microsoft 365 Business Premium offers a wealth of security features that can significantly enhance your organisation’s cybersecurity posture. By fully leveraging these tools, you can protect your business against a wide range of threats while also improving productivity and compliance.
Remember, cybersecurity is not a one-time effort but an ongoing process. Regularly review and update your security measures to stay ahead of evolving threats.
How Grassroots IT Can Help
At Grassroots IT, we specialise in helping businesses make the most of their Microsoft 365 investments. Our team of experts can:
- Assess your current security posture and identify areas for improvement
- Develop a customised implementation plan for M365 Business Premium security features
- Provide user training to ensure smooth adoption of new security measures
- Offer ongoing support and optimisation of your Microsoft 365 environment
Don’t leave your business vulnerable. Contact us today for a consultation, and let’s explore how we can enhance your cybersecurity with Microsoft 365 Business Premium.
Traditional security measures, while still important, are no longer sufficient to protect your organisation from sophisticated attacks. Enter Conditional Access Policies: a powerful tool in the Microsoft 365 suite that can significantly enhance your cybersecurity posture. In this post, we’ll explore how these policies work and why they are becoming an essential component of modern cybersecurity strategies.
What are Conditional Access Policies?
Conditional Access Policies are a feature of Microsoft 365 that allows you to control access to your organisation’s resources based on specific conditions. Think of them as smart gatekeepers for your digital assets. Instead of a simple “yes” or “no” to access requests, these policies consider various factors before granting access, such as:
- Who is requesting access?
- Where are they accessing from?
- What device are they using?
- What level of risk is associated with the access request?
By evaluating these factors in real-time, Conditional Access Policies can make nuanced decisions about whether to grant access, deny access, or require additional verification.
Current State of Cybersecurity
It’s not hyperbole to say that cybersecurity threats are growing exponentially, so before we dive deeper into Conditional Access Policies, let’s consider the current cybersecurity landscape.
- Remote work has expanded the attack surface for many organisations
- Phishing attacks are becoming increasingly sophisticated
- Ransomware incidents are on the rise, with potentially devastating consequences
- Data breaches can result in significant financial and reputational damage
In this environment, a static, one-size-fits-all approach to security is no longer adequate. Organisations need dynamic, context-aware security measures that can adapt to different situations and threat levels.
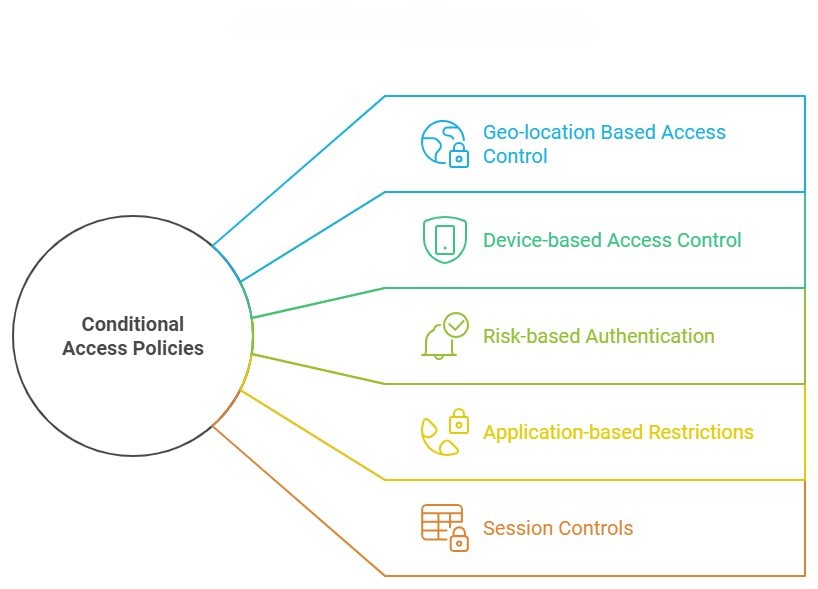
5 Ways Conditional Access Policies Enhance Your Security
Let’s explore five keyways that Conditional Access Policies can dramatically improve your cybersecurity posture:
1. Geo-location Based Access Control
One of the most powerful features of Conditional Access Policies is the ability to restrict access based on geographic location.
How it works: You can set policies that only allow access from specific countries or regions where your business operates. Attempts to access your resources from other locations can be blocked or require additional verification.
Real-world example:
- The Problem: An Australian based Veterinarian practice was receiving consistent login attempts to Microsoft 365 accounts from multiple locations around the world, causing concerns for an account breach.
- The Solution: Conditional Access policies were implemented to restrict user access to countries the Veterinarian practice traded from and dedicated IP restrictions of selected accounts that only needed to be accessed from the practices.
- The Result: Significant decrease in malicious user login attempts from blocked countries, and no accounts breaches for accounts only accessible from the practices.
2. Device-based Access Control
Ensuring that only trusted devices can access your resources is another crucial aspect of cybersecurity.
How it works: Conditional Access Policies can be set to only allow access from devices that are managed by your organisation or that meet certain security requirements.
Why it matters: This prevents scenarios where an employee might access sensitive company data from a personal device that lacks proper security measures. It also mitigates risks associated with lost or stolen devices. This is particularly important in the context of your organisation’s BYOD policy.
3. Risk-based Authentication
Microsoft’s cloud intelligence can detect signs of suspicious activity, which Conditional Access Policies can use to adjust authentication requirements in real-time.
How it works: If a login attempt is flagged as high-risk (e.g., it’s from an unfamiliar location or shows signs of bot activity), the policy can require additional verification steps or block access entirely.
Why it’s powerful: This adaptive approach means that routine, low-risk activities aren’t disrupted, but potential threats are met with appropriate security measures.
Real-world example:
- The Problem: A Mining organisation had an incident that almost allowed a fraudulent financial transaction to be processed.
- The Solution: Several Conditional Access policies were implemented, including Risk based access control, which uses Microsoft 365 intelligence to review user login and determine if there is any risk associated with the login and the level of risk for the login.
- The Result: All key financial and admin users are now assessed for each login, with Microsoft 365 determining any risk associated with the login session. Several key finance staff who were working via VPN were blocked when their sessions were re-authenticated after the VPN was disconnected, resulting in high-risk behaviour being detected, their accounts being blocked, and a password change required on login to unlock the account.
4. Application-based Restrictions
Not all company resources are equally sensitive. Conditional Access Policies allow you to set different access requirements for different applications or data types.
How it works: You might set a policy that allows broad access to the company intranet but requires multi-factor authentication and a company-managed device to access financial systems.
Real-world example:
- The Problem: An education institute required user access to email, Teams and SharePoint to be limited to only Microsoft applications on personal devices, allowing for greater control of the data.
- The Solution: Conditional Access policies that specifically target any access form a personal device and restricting access on this device to Microsoft Apps only.
- The Result: All users accessing the education Institute data for a personal device were required to install the Microsoft Company Portal App to allow management of institute data on their devices and enforce all policies applied to personal devices. This resulted in the institute finding multiple mobile devices that did not have any unlock code and multiple users who were accessing data from non-Microsoft apps that were not manageable via MDM.
5. Session Controls
Conditional Access doesn’t stop working after the initial authentication. It can also control what users can do during their sessions.
How it works: Policies can be set to limit activities like downloading, printing, or copying data from certain applications, even after a user has been granted access.
Why it matters: This can prevent data exfiltration attempts, where a bad actor who has gained access tries to download large amounts of sensitive data.
Real-world example:
- The Problem: An educational institute required that user access to email, Teams chat, and SharePoint documents could not be saved on personal devices.
- The Solution: Conditional Access policies that specifically target any access form a personal device, implementing session controls to block saving on these devices.
- The Result: Users accessing institute data on personal devices was blocked from saving emails, Teams chat and SharePoint documents, users were required to download and install the Microsoft Company Portal app and verify their account. allowing session controls on personal devices and blocking saving data outside of approved Microsoft apps.
Case Study: How our Client Improved Their Security with Conditional Access
Let’s look at how one of our clients, a mid-sized financial services firm, leveraged Conditional Access Policies to enhance their security:
Before implementing these policies, Company X had experienced several minor security incidents, including a case where an employee’s credentials were used to access company data from overseas during a time when the employee wasn’t traveling.
We helped them implement a comprehensive set of Conditional Access Policies, including:
- Geo-location restrictions
- Device management requirements
- Risk-based authentication
The result? In the six months following implementation:
- Suspicious access attempts decreased by 90%
- There were zero successful unauthorised access incidents
- Employee reports of account lockouts due to forgotten passwords decreased, thanks to the more nuanced, risk-based approach
While the IT team initially worried about user pushback, they found that most employees appreciated the additional security, especially once they understood how it protected both the company and their own personal information.
Conclusion
In an era where cyber threats are constantly evolving, static security measures are no longer enough. Conditional Access Policies provide a dynamic, intelligent approach to cybersecurity that can dramatically improve your organisation’s security posture.
By implementing these policies, you can:
- Reduce your risk of data breaches
- Gain greater control over how and where your company resources are accessed
- Adapt your security measures in real-time to respond to potential threats
- Improve overall compliance with data protection regulations
Remember, cybersecurity is not a one-time effort, but an ongoing process. Regularly reviewing and updating your Conditional Access Policies should be a key part of your overall security strategy.
How Grassroots IT Can Help
At Grassroots IT, we specialise in helping businesses leverage the full power of Microsoft 365, including advanced security features like Conditional Access Policies. Our team of experts can:
- Assess your current security posture
- Design and implement Conditional Access Policies tailored to your specific needs
- Provide ongoing support and optimisation of your policies
- Train your team on best practices for cybersecurity
Don’t wait for a security incident to occur. Take proactive steps to protect your organisation today. Contact us for a consultation, and let’s explore how we can enhance your cybersecurity with Conditional Access Policies.
Data protection isn’t just a nice-to-have—it’s a critical business imperative. Australian businesses face an increasingly complex web of regulations designed to safeguard personal information. But here’s the good news: if you’re using Microsoft 365, you’ve already got a powerful ally in your corner.
Let’s dive into how Microsoft 365 can help you navigate the choppy waters of data protection regulations in Australia, and how you can leverage its features to not just comply but thrive.
Understanding Australian Data Protection Regulations
Before we jump into the tech, let’s recap the regulatory landscape:
- The Privacy Act 1988 and its 13 Australian Privacy Principles (APPs) form the backbone of data protection law in Australia. These principles cover everything from the collection and use of personal information to its disclosure and security.
- The Notifiable Data Breaches (NDB) scheme requires organisations to notify affected individuals and the Office of the Australian Information Commissioner (OAIC) when a data breach is likely to result in serious harm. This means you need to have robust systems in place to detect, assess, and respond to data breaches quickly.
- Various industries have additional requirements, like APRA CPS 234 for financial services, which mandates specific information security practices.
Sounds daunting, right? Don’t worry—Microsoft 365 has got your back. Let’s explore how.
Microsoft 365 Compliance Center: Your Central Hub
Think of the Microsoft 365 Compliance Center as your control room for all things compliance. It gives you a bird’s-eye view of your compliance posture across your Microsoft 365 environment.
The Compliance Manager feature helps you track your progress towards meeting regulatory requirements. It provides a set of controls and improvement actions based on common regulations and standards. For each improvement action, you get step-by-step implementation guidance, which is incredibly helpful when you’re trying to navigate complex compliance requirements.
The Compliance Score, on the other hand, gives you a quantitative measure of your compliance efforts. It’s calculated based on the controls you’ve implemented and their relative importance. This score can be a great way to demonstrate your compliance efforts to stakeholders and identify areas for improvement.
Data Classification and Protection
One of the key requirements of APP 11 is ensuring the security of personal information. Microsoft 365’s sensitivity labels and Azure Information Protection allow you to classify and protect data based on its sensitivity.
Here’s how it works: You can create labels like “Confidential” or “Strictly Confidential” and define what happens when these labels are applied to documents or emails. For example, a “Strictly Confidential” label might automatically encrypt the document and restrict forwarding.
You can even use machine learning to automatically detect and label sensitive information like credit card numbers or health records. This means you can automatically apply protection actions like encryption or access restrictions to sensitive data, reducing the risk of unauthorised access.
Data Loss Prevention (DLP) Policies
Ever worried about sensitive information being shared accidentally? Microsoft 365’s DLP policies have got you covered. You can set up policies to prevent unauthorised sharing of sensitive information, aligning neatly with APP 6’s requirements around the use and disclosure of personal information.
For instance, you could create a policy that detects when a document contains multiple credit card numbers and blocks it from being shared outside your organisation. Or you could set up a policy that warns users when they’re about to send an email containing what looks like a tax file number.
These policies work across Microsoft 365, including in email, SharePoint, OneDrive, and Teams, providing comprehensive protection.
Retention and Deletion Policies
APP 11.2 requires the destruction or de-identification of personal information when it’s no longer needed. Microsoft 365’s retention and deletion policies allow you to automate this process, ensuring that data is retained only as long as necessary and then securely deleted.
You can create policies based on a variety of conditions. For example, you might set a policy to retain all emails for 7 years and then automatically delete them. Or you could create a policy that retains documents in a specific SharePoint site for 3 years after they were last modified.
These policies help ensure you’re not keeping data longer than necessary, which not only helps with compliance but can also reduce storage costs and minimise risk.
Auditing and Reporting
Many of the APPs require you to keep records of how personal information is handled. Microsoft 365’s comprehensive auditing capabilities and customisable reports make it easy to demonstrate compliance when needed.
The unified audit log records user and admin activities across many Microsoft 365 services. You can search this log to investigate potential security or compliance issues, or to respond to legal or regulatory requests.
You can also create custom reports to track specific activities or compliance metrics. These reports can be invaluable when you need to demonstrate your compliance efforts to auditors or regulators.
Secure Access and Identity Management
Azure Active Directory, part of the Microsoft 365 suite, provides robust identity and access management capabilities. Implementing features like multi-factor authentication can significantly enhance your data security, helping you meet the requirements of APP 11.
But it goes beyond just multi-factor authentication. Azure AD also offers features like:
- Conditional Access, which allows you to create policies that either allow or block access based on factors like user location, device status, and real-time risk detection.
- Privileged Identity Management, which helps you minimise the number of people who have access to secure information or resources, reducing the risk of malicious actions.
- Access Reviews, which allow you to regularly review and recertify user access, ensuring that users only have the access they need.
Responding to Data Breaches
The NDB scheme requires prompt notification of serious data breaches. Microsoft 365’s advanced threat protection features, including Insider Risk Management and Communication Compliance, can help you detect potential breaches early.
Insider Risk Management uses machine learning to identify potential insider risks, like data leaks or intellectual property theft. It analyses signals across Microsoft 365, spotting patterns that might indicate a problem.
Communication Compliance helps you detect, capture, and take remediation actions for inappropriate messages. For example, it can detect offensive language, sensitive information sharing, or conflicts of interest in communications.
These tools give you a head start in responding and notifying affected parties if necessary, helping you meet the tight timeframes required by the NDB scheme.
Wrapping Up
Microsoft 365 offers a comprehensive set of tools to help you meet Australian data protection regulations. But remember, these tools are only effective when properly configured and managed. It’s like having a high-performance car—it’s great, but you need to know how to drive it to get the most out of it.
That’s where we come in. At Grassroots IT, we’ve been helping businesses navigate the complexities of IT and compliance for almost two decades. We’re not just here to set up your tech—we’re here to help you use it strategically to drive your business forward.
Want to know how well your current setup measures up? We offer a comprehensive Business Technology Review that can help you identify gaps in your compliance posture and opportunities for improvement. Get in touch with us today, and let’s make sure your business isn’t just compliant, but thriving.
Remember, in the world of data protection, an ounce of prevention is worth a pound of cure. Don’t wait for a breach to start taking compliance seriously—your business (and your customers) will thank you for it. With the right tools and expertise, you can turn compliance from a burden into a competitive advantage. Let’s make it happen together.
Remote work has become more than just a trend – it’s now a fundamental part of how many Australian businesses operate. While this shift brings numerous benefits, it also presents new challenges in data security. With team members accessing sensitive information from various locations and devices, how can you ensure your data remains protected? This is where Data Loss Prevention (DLP) becomes crucial.
The Remote Work Security Challenge
Remote work has expanded the traditional network perimeter, making it more difficult to control and monitor data access and movement. Your team members might be working from home in Brisbane, from a client’s office in Sydney or a cafe in Melbourne. They’re likely using a mix of company-issued and personal devices, connecting through various networks of varying security levels.
In this distributed environment, the risks of data leaks – both accidental and intentional – increase significantly. An employee might inadvertently send sensitive information to their personal email for easier access or to save confidential documents to an unsecured cloud storage service. Without proper safeguards, your valuable business data could be exposed to unauthorised access or breaches.
Enter Data Loss Prevention (DLP)
DLP is a set of tools and strategies designed to detect potential data breaches and prevent them by monitoring, detecting, and blocking sensitive data while in use, in motion, and at rest. In a remote work context, DLP becomes your virtual security guard, ensuring that your data is protected regardless of where your team members are located.
Key DLP Strategies for Remote Work
- Content Awareness: Modern DLP solutions can identify sensitive information based on predefined patterns, keywords, or file properties. This means you can set up policies to protect specific types of data, such as financial records or client information, regardless of where it’s stored or how it’s being accessed.
- Context-Based Policies: DLP isn’t just about blocking all data movement. It’s about understanding the context of data use. For example, you might impose restrictions on documents labelled as “Top Secret,” block emails sent to specific domains, or prevent sharing files with certain extensions. You can also tailor access controls based on the sensitivity of the data and the specific circumstances of its use.
- User Education and Alerts: One of the most powerful features of DLP is its ability to educate users in real-time. When an employee is about to violate a policy, the DLP system can alert them, explaining why the action is risky and suggesting secure alternatives.
- Endpoint Protection: With remote work, every device becomes an endpoint that needs protection. DLP can be extended to laptops, tablets, and even smartphones, ensuring that data is protected even on personal devices used for work.
- Cloud Application Control: As remote teams rely heavily on cloud applications, DLP can monitor and control data sharing across these platforms, preventing unauthorised sharing or downloads.
Implementing DLP for Remote Work: A Hypothetical Case Study
Let’s consider a mid-sized engineering firm based in Brisbane. With their team of 50 now working remotely, they implemented a DLP solution to secure their client data and creative assets. Here’s how they approached it:
- They started by categorising their data, identifying what was most sensitive (e.g., client strategies, financial information) and what was less critical.
- They set up DLP policies to monitor emails and file transfers, alerting employees if they attempted to send sensitive information to personal email addresses or unauthorised third parties.
- For their design team working with large files, they implemented policies that allowed the use of approved cloud storage solutions but blocked uploads to personal accounts.
- They used endpoint DLP on all company-issued laptops, ensuring that sensitive data couldn’t be copied to USB drives or other external storage without approval.
- The DLP system was configured to provide real-time education to employees, explaining why certain actions were blocked and suggesting secure alternatives.
The (hypothetical) result? In the first month alone, the agency prevented several potential data leaks, including an instance where a new employee almost sent a confidential client brief to their personal email. The system not only blocked the transfer but also educated the employee about the proper protocols for handling sensitive information.
Best Practices for DLP in Remote Work Environments
- Start with Clear Policies: Before implementing technical solutions, ensure you have clear, written policies about data handling in remote work situations. Make sure all employees understand these policies.
- Use a Graduated Approach: Start with monitoring and alerting before moving to more restrictive blocking policies. This allows you to understand your data flow and refine your approach.
- Focus on User Experience: The goal is to protect data without hindering productivity. Choose DLP solutions that offer seamless user experiences and integrate well with your existing tools.
- Regular Training: Complement your DLP implementation with regular security awareness training. The more your team understands about data security, the more effective your DLP strategy will be.
- Continuous Monitoring and Adjustment: The remote work landscape and potential threats are continually evolving. Regularly review and adjust your DLP policies to ensure they remain effective.
Conclusion
As remote work continues to be a significant part of our business landscape, protecting your data has never been more crucial. DLP provides a powerful set of tools to secure your sensitive information, regardless of where your team members are working from. By implementing a well-thought-out DLP strategy, you can enjoy the benefits of remote work while maintaining the security of your valuable business data.
Are you unknowingly overspending on your Microsoft 365 licences? You’re not alone. But the impact of poor licence management goes far beyond just your bottom line.
As IT professionals, we’ve observed that licence management is often overlooked, despite its significant impact on a company’s operational efficiency, security posture, and overall productivity. Let’s explore why this matters and how proper management can benefit your business.
Common Ways Businesses Mismanage Microsoft 365 Licences
Here are 4 common ways businesses mismanage their Microsoft 365 licences:
- Retaining inactive licences: Licenses can easily remain assigned to former employees or unused accounts. Beyond the obvious cost implications, this poses a significant security risk, potentially leaving access points open to unauthorised use.
- Incorrect licence mix: Not all licences are created equal. An imbalanced mix can lead to overpayment or lack of crucial features, impacting costs, productivity, and your ability to implement critical security measures. .
- Overprovisioning features: Many staff members are assigned comprehensive licences when they only require basic functionalities. This not only results in unnecessary expenditure but can also overwhelm users with unused features, potentially reducing productivity.
- Neglecting regular reviews: Microsoft frequently updates their offerings. Without regular reviews, you may miss out on new features or security enhancements that could significantly benefit your business operations.
Why Effective Licence Management Matters
It’s crucial to understand that effective licence management isn’t just about minimising costs. It’s about optimising your Microsoft 365 environment to align with your business needs and strategic goals. Here’s why it truly matters:
- Enhanced Security: Proper licence management ensures you have access to the latest security features, reducing your organisation’s vulnerability to cyber threats. We recommend the Microsoft Business Premium plan as the sweet spot for both price and features, particularly around security & compliance
- Improved Compliance: Certain licence types include advanced compliance tools. Having the right licences helps you meet regulatory requirements more effectively. For example, the cheaper Microsoft 365 Business Standard plan doesn’t include features such as Unified Audit Logging and Sensitivity Labels, both of which are useful for compliance.
- Increased Productivity: When users have the right tools for their roles, they can work more efficiently. Proper licence allocation ensures everyone has what they need – no more, no less. .
- Future-Proofing: Regular licence reviews help you stay ahead of technological changes, ensuring your business is always leveraging the most current and beneficial features. .
- Strategic IT Alignment: Licence management is a key part of aligning your IT capabilities with your broader business strategy, driving digital transformation and competitive advantage.
Proper licence management doesn’t need to be onerous, but it does require ongoing attention, expertise, and strategic planning. It’s about understanding your current needs, anticipating future requirements, and aligning your licensing strategy with your broader IT and business goals.
If you’re not actively managing your Microsoft 365 licences, you’re likely missing opportunities for cost savings, operational improvements, and enhanced security. More importantly, you may be compromising on tools that could drive your business forward in an increasingly digital world.
Getting Started with Licence Management
The first step towards improved licence management is to understand what licences you currently have in place. This is easily done from within Microsoft 365 Admin, or by asking your IT team to produce a report for you.
From there, you can review your current licence assignment against actual usage and business needs. This will help identify any discrepancies, such as overprovisioning or inactive licences still assigned to former employees.
At Grassroots IT, we believe that technology should be a strategic enabler for your business. Effective licence management is a key part of this strategy. It ensures you’re getting the most value from your Microsoft 365 investment, both in terms of cost-efficiency and operational capability.
Ready to stop overspending and start optimising your Microsoft 365 environment? Let’s have a conversation about how we can help you align your licences with your business needs and goals, ensuring you’re not just saving money, but setting your business up for future success.
You’ve likely heard buzzwords like “cloud services” and “mobile device management” floating around, and perhaps “Microsoft Intune” has come up in conversations with your IT provider or tech-savvy colleagues. But what exactly is Intune, and why should you care about it? Let’s break it down in plain English, so you can understand how this tool might benefit your business – without needing a degree in computer science.
The Basics: What is Microsoft Intune?
Microsoft Intune is a cloud-based service that helps businesses manage their devices and applications. Think of it as a central control panel for all the phones, tablets, and computers your team uses for work. It’s part of Microsoft’s broader suite of business tools, integrating seamlessly with other Microsoft 365 products, and is rapidly becoming a core part of how many businesses manage their IT systems.
What Does Intune Do?
Intune’s capabilities can be broken down into three main categories: Device Management, App Management, and Security.
Device Management
Intune gives you control over how company devices such as laptops are used. With Intune, you can set password requirements to ensure all devices have strong, secure passwords. You can control which apps can be installed, preventing potentially harmful or unproductive apps from being used on work devices. Intune also allows you to configure device settings, setting up email, Wi-Fi, VPN, and other settings automatically. Perhaps most crucially, if a device is lost or stolen, you can remotely wipe data from it, protecting your company’s sensitive information.
App Management
When it comes to apps, Intune is your central command centre. You can push necessary apps to all devices, ensuring everyone has the tools they need to do their job effectively. Intune also allows you to control which apps can access company data, keeping your sensitive information safe. It can update apps automatically, keeping everyone on the latest, most secure versions. And when an employee leaves the company, Intune makes it easy to remove business apps and data from their device, protecting your intellectual property.
Security
Security is paramount, and Intune has you covered. Microsoft Intune is a robust solution for managing and securing your organisation’s devices and data. It ensures that all devices are up to date with the latest security patches and updates, reducing vulnerabilities. Intune also integrates seamlessly with Microsoft Defender and other security products, creating a comprehensive security ecosystem. By enforcing policies such as data encryption and remote wipe, Intune protects sensitive information even if a device is lost or stolen. Additionally, it links with Entra ID to manage multi-factor authentication and conditional access policies, preventing unauthorised access to company resources. With Intune, you can confidently safeguard your business data against a wide range of security threats.
Why Should You Care?
Now that we understand what Intune does, let’s talk about why it matters for your business.
Intune offers flexibility, working with both company-owned devices and personal devices in a Bring Your Own Device (BYOD) environment. This means you can secure your data whether your team is using company laptops or their own smartphones.
Simplicity is another key benefit. Instead of your IT team dealing with each device individually, they can manage everything from one place. This can save significant time and reduce headaches.
Security is a major advantage of Intune. It allows you to protect your business data without making life difficult for your team. Intune’s security features work in the background, allowing your team to focus on their work rather than wrestling with cumbersome security protocols.
Productivity gets a boost with Intune. By ensuring your team has the right tools and access, wherever they’re working from, Intune provides seamless access to business resources while maintaining control.
Finally, Intune can be cost-effective. By managing devices and apps centrally, you can often reduce your overall IT costs and simplify budgeting.
Is Intune Right for Your Business?
Intune can be particularly useful in several scenarios. If you have a mobile workforce that works from various locations or uses multiple devices, Intune can help keep everyone connected and secure. If you’re concerned about data security (and in this day and age, who isn’t?), Intune provides robust security features to protect your business data.
If you’re tired of hearing about individual device issues and want to simplify your IT management, Intune can streamline your processes. If you’re already using other Microsoft 365 products, Intune integrates seamlessly, creating a cohesive ecosystem. And if you’re supporting a bring-your-own-device (BYOD) environment, Intune allows you to secure company data on personal devices without infringing on employee privacy.
Related: Securing Your Remote Workforce with Entra ID and Intune | Grassroots IT
Real-World Example
Let’s consider a scenario to see how Intune works in practice:
Imagine you run a small marketing agency with 20 employees. Half of your team works in the office, while the others work remotely or at client sites. Some use company laptops, others use their personal devices.
With Intune, you can ensure all devices (company-owned and personal) that access business data have the necessary security measures in place. Your team can easily access the apps and data they need, whether they’re in the office or at a client site. If someone’s device is lost or stolen, your IT team can quickly remove business data from that device. When you onboard a new employee, they can automatically set up the device with all necessary apps and settings. And if an employee leaves, they can remove business apps and data from their device without touching their personal information.
Wrapping Up
Microsoft Intune is a powerful tool that can help streamline your IT management, enhance your security, and boost your team’s productivity. While it may seem complex at first, the benefits it brings to your business can be significant.
Remember, good IT shouldn’t give you headaches – it should solve them. Intune is just one of the many tools that can help make your business technology work for you, not against you.
At Grassroots IT, we’ve been helping businesses like yours leverage tools like Intune for nearly two decades. We understand that every business is unique, and we’re here to help you navigate the world of modern IT solutions. Whether you’re ready to implement Intune or just want to learn more, we’d be happy to chat about how it could work for your specific needs.
Technology should be an enabler for your business, not a barrier. Let’s work together to make sure your IT is helping your business thrive.
The Power of Integrated Lifecycle Management
Managing the lifecycle of users and devices is a critical aspect of IT operations. From the moment a new employee joins your organisation to the day they leave, and from when a device is first enrolled to when it’s retired, there are numerous considerations involved in maintaining a secure, efficient, and productive IT environment.
Two powerful tools in the Microsoft 365 suite can help streamline this process: Entra ID (formerly Azure AD) and Intune. In this post, we’ll explore how these services work together to provide a comprehensive lifecycle management solution for your users and devices.
User Creation and Onboarding
The journey begins when a new user joins your organisation. Entra ID facilitates this process through a series of steps:
- Create the user account: Use the Azure portal to manually create the account, or leverage PowerShell scripts or HR system integration for automatic account creation
- Assign licenses and access rights: Grant the necessary licenses (such as Microsoft 365 Business Premium) and provide access to required resources. For organisations with defined roles, Entra ID’s group-based licensing can streamline this process.
- Enable multi-factor authentication (MFA): As a crucial security measure, add users to an MFA registration campaign to enforce MFA setup. Entra ID offers various options, including the Microsoft Authenticator app, SMS, or phone calls.
- Configure conditional access policies: Set up policies to control resource access based on specific conditions. For new users, you might require a password change on first login or restrict access to certain apps until they’ve completed necessary training.
- Provide necessary information to the user: Share login credentials, MFA setup instructions, and any other relevant information with the new user.
To streamline this process, consider creating a standardised onboarding workflow that automates as many of these steps as possible. This approach not only saves time but also ensures consistency in how new users are set up across your organisation.
Remember, user onboarding is more than just technical setup. It’s an opportunity to make a great first impression and set new team members up for success. Consider incorporating steps like sending a welcome email, scheduling an IT orientation session, or providing a digital welcome pack with key information about your organisation’s IT practices and policies.
Device Enrolment
Once a user account is set up, the next step is often to get them set up with a device such as a laptop. This is where Intune shines, offering a range of enrolment methods to suit different organisational needs and device types.
Company-Owned Devices
For company-owned devices, Intune allows you to pre-configure enrolment profiles. This proactive approach ensures that devices are compliant with your policies from the moment they’re turned on, saving time and reducing security risks.
BYOD Support
For organisations embracing Bring Your Own Device (BYOD) policies, Intune also supports personal device enrolment. In these scenarios, you can apply different policies that strike a balance between organisational security needs and user privacy.
Windows Autopilot
It’s worth mentioning Windows Autopilot as part of the same discussion as Intune and Entra ID. Windows Autopilot simplifies the device setup process, making new devices ready to use with minimal IT intervention. Here’s how it works:
- Devices are pre-registered with your organisation (often by the hardware vendor).
- When first turned on, the device automatically configures itself.
- It joins your Azure AD, enrols in Intune, and applies your predefined settings and policies.
Autopilot is particularly useful for remote workers, as devices can be shipped directly to them, ready to use out of the box. This approach saves time for IT teams and ensures consistency across all devices.
Ongoing Management
Once users are set up and devices are enrolled, the focus shifts to ongoing management. This is where the true power of Intune and Entra ID’s integration becomes apparent, offering a comprehensive suite of tools for maintaining security, compliance, and efficiency.
Security Policies
Intune allows you to create and apply security policies to your devices. These policies can cover a wide range of security measures, including:
- Device encryption requirements
- Restrictions on certain device features
By applying these policies, you can ensure that all devices, whether company-owned or personal, meet your organisation’s security standards.
App Management
With Intune, you gain granular control over app deployment and management. You can:
- Deploy both store apps and line-of-business apps to your devices
- Manage app updates to ensure all devices are running the latest, most secure versions
- Set up app protection policies to safeguard company data within applications
This level of control ensures that your users have access to the tools they need while maintaining security and compliance.
Compliance Monitoring
Intune continuously monitors devices for compliance with your policies. If a device falls out of compliance, you can configure automated actions, such as blocking access to company resources. This real-time monitoring and response capability helps maintain your security posture without constant manual oversight.
Access Management
As users’ roles change within your organisation, you can use Entra ID to adjust their access rights accordingly. This includes:
- Modifying group memberships to grant or revoke access to specific resources
- Updating license assignments as needed
- Managing privileged access through Entra ID’s Privileged Identity Management feature
This dynamic access management ensures that users always have the right level of access for their current role, no more and no less.
Through the integrated use of Intune and Entra ID, ongoing management becomes a dynamic, responsive process. It allows you to maintain security and compliance while providing users with the tools and access they need to be productive. This balance of security and usability is key to a successful modern workplace strategy.
Embracing Comprehensive Lifecycle Management
The integration of Entra ID and Intune provides a powerful solution for managing the entire lifecycle of users and devices in your organisation. From streamlined user onboarding to simplified device enrolment, and from robust ongoing management to comprehensive security and compliance features, these tools offer a holistic approach to modern IT management.
By implementing this integrated lifecycle management approach, organisations can:
- Enhance security posture through consistent policy application and advanced threat protection
- Improve efficiency by automating many routine IT tasks
- Ensure compliance with regulatory requirements through built-in features and detailed reporting
- Provide a better user experience with seamless access to necessary resources
- Adapt more quickly to changing business needs and evolving security threats
Particularly in a world where remote work is increasingly common, and security threats are ever-present, such a comprehensive approach to lifecycle management is no longer a luxury—it’s a necessity.
Whether you’re just starting your journey with Microsoft 365 or looking to optimise your existing setup, Grassroots IT is here to help. We can assess your current environment, design a tailored implementation strategy, and provide ongoing support to ensure your lifecycle management processes continue to meet your evolving needs.
The digital landscape has seen a fundamental shift in how businesses operate, with remote work becoming more than just a trend. While this flexibility brings numerous benefits, it also introduces new challenges in securing business data and maintaining a robust cybersecurity posture.
As your team members access sensitive information from various locations and devices, how can you ensure that your business data remains protected? Enter Microsoft Entra ID (formerly Azure AD) and Intune—two powerful tools that, when combined, provide a comprehensive solution for securing your remote workforce.
Understanding the Security Challenges of Remote Work
Before we dive into the solutions, let’s take a moment to understand the unique security challenges that come with remote work:
- Increased attack surface: With devices operating outside the corporate network, not only are traditional security controls such as corporate firewalls rendered powerless, but there are also more potential entry points for cybercriminals. This can include unsecured Wi-Fi networks, personal devices, and even the use of public computers.
- Data leakage risks: The use of personal devices for work purposes can lead to inadvertent data exposure. For example, a team member may unintentionally save sensitive company data on their personal cloud storage or accidentally share confidential information with unauthorised individuals.
- Policy enforcement difficulties: Maintaining consistent security policies across a distributed workforce can be challenging. Traditional methods of enforcing policy, such as Active Directory, are unreliable at best with a remote workforce. This can lead to inconsistent security practices and increased vulnerability.
- Shadow IT: Remote workers might resort to using unauthorised applications or services to get their work done, potentially exposing company data to unsecured platforms. This “shadow IT” can be difficult to detect and control in a remote environment.
Microsoft Entra ID: The Foundation of Identity Security
At the heart of securing your remote workforce is robust identity management. This is where Microsoft Entra ID shines.
Entra ID is a cloud-based identity and access management service that forms the backbone of security for Microsoft 365 and many other cloud applications. For securing and protecting remote workers, Entra ID offers several key benefits:
- Single Sign-On (SSO): Allows users to access multiple applications with one set of credentials, improving both security and user experience. This reduces the likelihood of employees using weak or repeated passwords across multiple services.
- Multi-Factor Authentication (MFA): Adds an extra layer of security by requiring two or more verification methods to access resources. This significantly reduces the risk of unauthorised access, even if passwords are compromised.
- Conditional Access: Enables you to control access to your apps and data based on identity, device, and risk signals. For example, you can require additional authentication steps for access from unfamiliar locations or devices.
By implementing Entra ID, you create a strong foundation for securing your remote workforce’s identities and controlling access to your business resources. And the good news is, if you already have a Microsoft 365 subscription, you already have access to Entra ID.
Intune: Comprehensive Device Management for Remote Workers
While Entra ID secures identities, Microsoft Intune takes care of device and application management. Intune is a cloud-based service that focuses on mobile device management (MDM) and mobile application management (MAM).
Key features of Intune include:
- Device enrolment: Easily enrol and manage devices across various platforms (Windows, iOS, Android). This allows you to maintain control over both company-owned and personal devices used for work, even allowing you to remote-wipe a device in the event it becomes lost.
- Application management: Deploy and manage apps on remote devices, ensuring your team has the tools they need. This includes the ability to push required apps to devices and remove them when necessary.
- Device compliance: Set rules, assess device compliance and deploy policies to protect company data. For instance, you can require devices to have up-to-date antivirus software and encrypted storage.
With Intune, you can ensure that all devices accessing your business data—whether company-owned or personal—meet your security standards.
Combining Entra ID and Intune for Robust Security
The real magic happens when you combine the powers of Entra ID and Intune. Together, they provide a comprehensive security solution for your remote workforce:
- Conditional Access policies: Use Entra ID’s Conditional Access in conjunction with Intune’s device compliance to control resource access based on user, device, and risk factors. For example, you can require that devices be managed by Intune and compliant with your policies before allowing access to company resources.
- App protection policies: Protect your data at the application level, preventing unauthorised sharing or saving of company information. This is particularly useful for BYOD scenarios where you need to separate personal and work data on the same device.
- Automated enforcement: Ensure compliance requirements are met on remote devices without manual intervention. Non-compliant devices can be automatically blocked from accessing company resources until they meet the required standards.
Conclusion
Securing your remote workforce doesn’t have to be a headache. With Microsoft Entra ID and Intune, you have a powerful combination of tools at your disposal to protect your business data, manage devices, and ensure compliance—all while providing a seamless experience for your remote team.
By implementing these solutions, you’re not just reacting to the challenges of remote work; you’re proactively building a secure, flexible, and productive work environment for the future. You’re empowering your team to work from anywhere, without compromising on security.
Ready to take the next step in securing your remote workforce? At Grassroots IT, we’ve been helping businesses like yours navigate the complexities of IT security for almost 20 years. Get in touch today for a free consultation and let’s explore how we can empower your remote team while keeping your data safe.
Limited resources, diverse stakeholder needs, and the pressure to demonstrate impact – all contribute to the complexity of non-profit operations and emphasise the critical need for efficient workflows. Fortunately, Microsoft 365 offers a suite of powerful tools that can help streamline processes, enhance collaboration, and boost productivity. Let’s explore five key Microsoft 365 tools that can transform how your non-profit works.
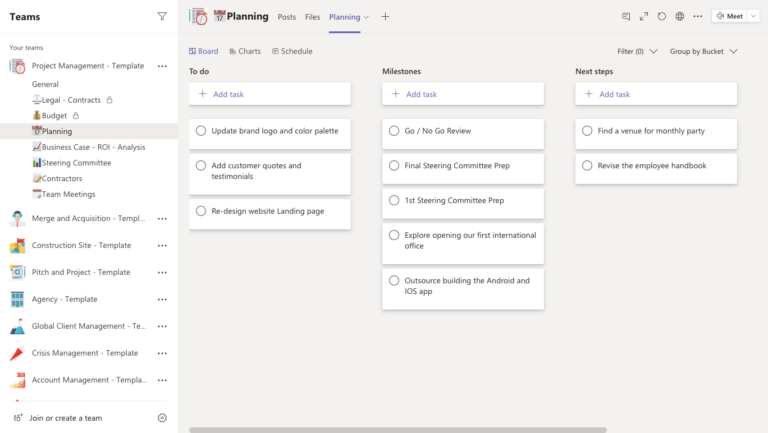
1. Microsoft Planner: Streamline Task Management
Microsoft Planner is a user-friendly task management tool that can significantly improve your team’s productivity. In fact, here at Grassroots IT we use Planner on a daily basis to keep team meetings organised and track actions & accountabilities.
Here’s how it can benefit your non-profit:
- Visual Task Boards: Create Kanban-style boards to visualize your projects and track progress at a glance.
- Security Considerations: Running an unsupported operating system can expose your business to increased security risks, as Microsoft will no longer release security fixes and updates for issues that are discovered. Cybercriminals often target systems that no longer receive regular security updates.
- Integration: Planner integrates seamlessly with other Microsoft 365 tools, making it easy to attach documents from SharePoint or OneDrive, or discuss tasks in Teams.
By using Planner, your non-profit can ensure that all team members are aligned on project goals, deadlines, and responsibilities, leading to more efficient project execution.
2. SharePoint: Centralise Document Management
SharePoint is a powerful platform for document management and collaboration. Not only that, but in preparation for AI tools such as Microsoft Copilot, SharePoint is the person place to store company information. For non-profits, it offers several key advantages:
- Centralised Document Storage: Create a single source of truth for all your organisation’s documents, accessible from anywhere
- Version Control: Track changes and maintain a history of document revisions, crucial for maintaining accuracy in reports and proposals
- Intranet Capabilities: Build internal websites to share news, updates, and resources across your organisation
- Granular Permissions: Control who can access, edit, or share specific documents or sites, ensuring data security
With SharePoint, your non-profit can improve information flow, reduce time spent searching for documents, and enhance collaboration across departments.
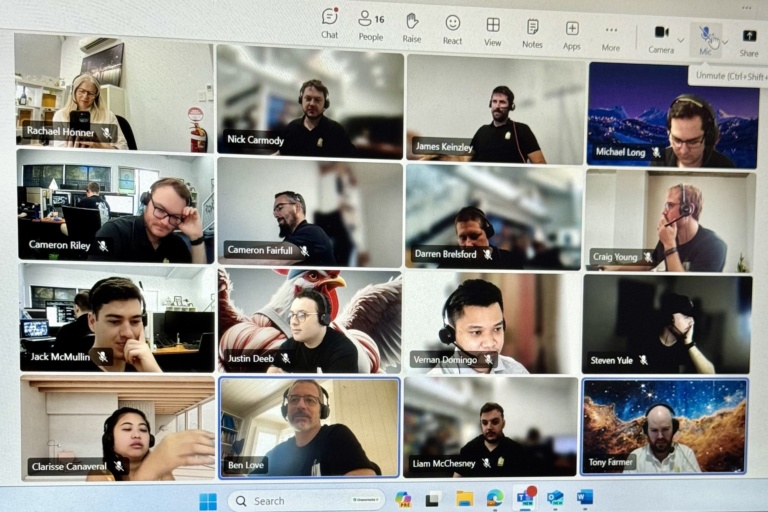
3. Microsoft Teams: Enhance Communication and Collaboration
Microsoft Teams is a hub for teamwork, bringing together chat, video meetings, file storage, and application integration. At Grassroots IT with a diverse team spread across five countries, we rely heavily on Teams to keep our people connected.
For non-profits, Teams can:
- Facilitate Remote Work: Host virtual meetings, share screens, and collaborate in real-time, regardless of team members’ locations
- Organise Conversations: Create channels for different projects or departments, keeping discussions focused and easily searchable
- Integrate Apps: Bring other Microsoft 365 tools and third-party apps into your Teams workspace for a seamless experience?
- External Collaboration: Invite volunteers, donors, or partners to specific teams or channels, fostering better stakeholder engagement
By leveraging Teams, your non-profit can break down communication silos and create a more connected, collaborative work environment.
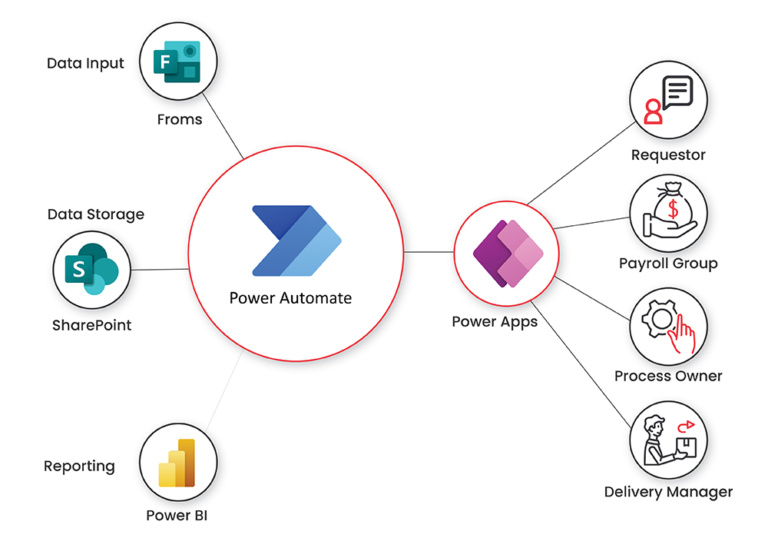
4. Power Automate: Streamline Repetitive Tasks
Power Automate (formerly known as Flow) is a powerful tool for creating automated workflows. Here’s how it can benefit your non-profit:
- Time-Saving Automation: Automate repetitive tasks like data entry, email notifications, or approval processes.
- Cross-Application Workflows: Create flows that work across different Microsoft 365 apps and even third-party services.
- Triggered Actions: Set up automated actions based on specific triggers, such as sending a thank-you email when a new form submission is received
- Templates: Use pre-built templates to quickly implement common automation scenarios.
By automating routine tasks with Power Automate, your non-profit can free up valuable time for more strategic, mission-focused work.
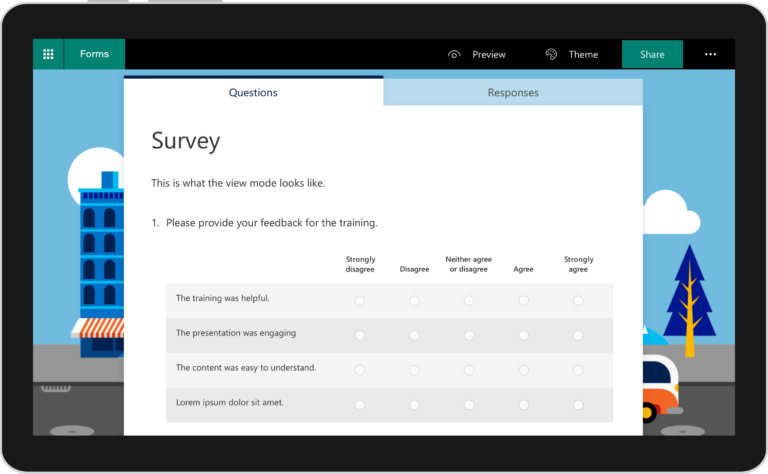
5. Microsoft Forms: Streamline Data Collection and Surveys
Microsoft Forms is a simple yet powerful tool for creating surveys, quizzes, and polls. For non-profits, it offers several benefits:
- Easy-to-Create Surveys: Build professional-looking forms and surveys without any technical expertise
- Real-Time Analytics: Get instant insights with automatic charts that update as responses come in
- Integration with Other Tools: Easily export data to Excel for deeper analysis or use Power Automate to trigger actions based on form responses
- Accessible and Responsive: Forms work on any device, making it easy to collect data from volunteers, donors, or beneficiaries in the field
- Multilingual Support: Create forms in multiple languages to reach diverse audiences
Microsoft Forms can help your non-profit gather valuable feedback, conduct needs assessments, or even manage event registrations with ease.
Final Thoughts
These five Microsoft 365 tools – Planner, SharePoint, Teams, Power Automate, and Forms – offer a powerful ecosystem to revolutionize your non-profit’s workflow. By leveraging these tools, you can enhance collaboration, streamline processes, and ultimately increase your organisation’s impact.
Remember, the key to success with these tools lies in thoughtful implementation and user adoption. Consider starting with one or two tools that address your most pressing needs, and gradually expand your use as your team becomes more comfortable with the new systems.
At Grassroots IT, we’re here to help you navigate the world of Microsoft 365 and find the best solutions for your non-profit’s unique needs. Reach out to us to learn more about how we can support your journey to a more efficient, tech-enabled workflow.