Traditional security measures, while still important, are no longer sufficient to protect your organisation from sophisticated attacks. Enter Conditional Access Policies: a powerful tool in the Microsoft 365 suite that can significantly enhance your cybersecurity posture. In this post, we’ll explore how these policies work and why they are becoming an essential component of modern cybersecurity strategies.
What are Conditional Access Policies?
Conditional Access Policies are a feature of Microsoft 365 that allows you to control access to your organisation’s resources based on specific conditions. Think of them as smart gatekeepers for your digital assets. Instead of a simple “yes” or “no” to access requests, these policies consider various factors before granting access, such as:
- Who is requesting access?
- Where are they accessing from?
- What device are they using?
- What level of risk is associated with the access request?
By evaluating these factors in real-time, Conditional Access Policies can make nuanced decisions about whether to grant access, deny access, or require additional verification.
Current State of Cybersecurity
It’s not hyperbole to say that cybersecurity threats are growing exponentially, so before we dive deeper into Conditional Access Policies, let’s consider the current cybersecurity landscape.
- Remote work has expanded the attack surface for many organisations
- Phishing attacks are becoming increasingly sophisticated
- Ransomware incidents are on the rise, with potentially devastating consequences
- Data breaches can result in significant financial and reputational damage
In this environment, a static, one-size-fits-all approach to security is no longer adequate. Organisations need dynamic, context-aware security measures that can adapt to different situations and threat levels.
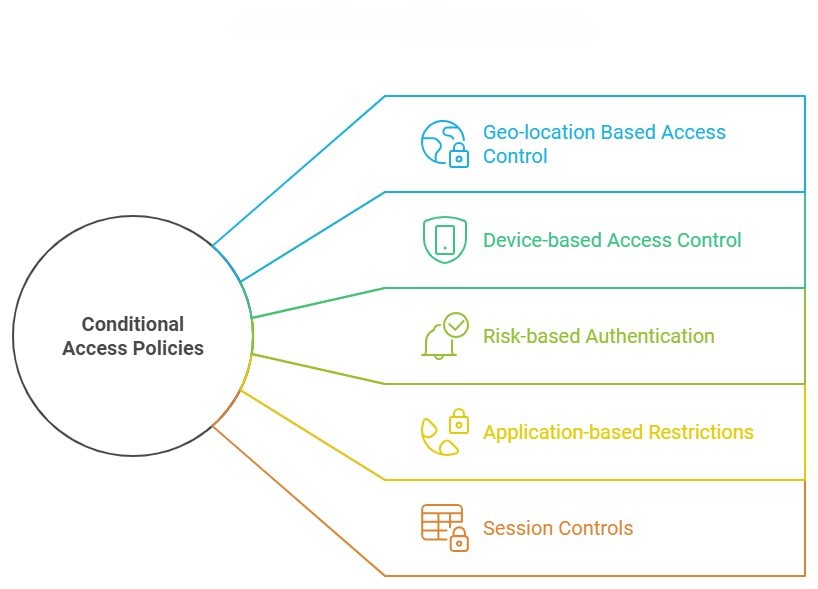
5 Ways Conditional Access Policies Enhance Your Security
Let’s explore five keyways that Conditional Access Policies can dramatically improve your cybersecurity posture:
1. Geo-location Based Access Control
One of the most powerful features of Conditional Access Policies is the ability to restrict access based on geographic location.
How it works: You can set policies that only allow access from specific countries or regions where your business operates. Attempts to access your resources from other locations can be blocked or require additional verification.
Real-world example:
- The Problem: An Australian based Veterinarian practice was receiving consistent login attempts to Microsoft 365 accounts from multiple locations around the world, causing concerns for an account breach.
- The Solution: Conditional Access policies were implemented to restrict user access to countries the Veterinarian practice traded from and dedicated IP restrictions of selected accounts that only needed to be accessed from the practices.
- The Result: Significant decrease in malicious user login attempts from blocked countries, and no accounts breaches for accounts only accessible from the practices.
2. Device-based Access Control
Ensuring that only trusted devices can access your resources is another crucial aspect of cybersecurity.
How it works: Conditional Access Policies can be set to only allow access from devices that are managed by your organisation or that meet certain security requirements.
Why it matters: This prevents scenarios where an employee might access sensitive company data from a personal device that lacks proper security measures. It also mitigates risks associated with lost or stolen devices. This is particularly important in the context of your organisation’s BYOD policy.
3. Risk-based Authentication
Microsoft’s cloud intelligence can detect signs of suspicious activity, which Conditional Access Policies can use to adjust authentication requirements in real-time.
How it works: If a login attempt is flagged as high-risk (e.g., it’s from an unfamiliar location or shows signs of bot activity), the policy can require additional verification steps or block access entirely.
Why it’s powerful: This adaptive approach means that routine, low-risk activities aren’t disrupted, but potential threats are met with appropriate security measures.
Real-world example:
- The Problem: A Mining organisation had an incident that almost allowed a fraudulent financial transaction to be processed.
- The Solution: Several Conditional Access policies were implemented, including Risk based access control, which uses Microsoft 365 intelligence to review user login and determine if there is any risk associated with the login and the level of risk for the login.
- The Result: All key financial and admin users are now assessed for each login, with Microsoft 365 determining any risk associated with the login session. Several key finance staff who were working via VPN were blocked when their sessions were re-authenticated after the VPN was disconnected, resulting in high-risk behaviour being detected, their accounts being blocked, and a password change required on login to unlock the account.
4. Application-based Restrictions
Not all company resources are equally sensitive. Conditional Access Policies allow you to set different access requirements for different applications or data types.
How it works: You might set a policy that allows broad access to the company intranet but requires multi-factor authentication and a company-managed device to access financial systems.
Real-world example:
- The Problem: An education institute required user access to email, Teams and SharePoint to be limited to only Microsoft applications on personal devices, allowing for greater control of the data.
- The Solution: Conditional Access policies that specifically target any access form a personal device and restricting access on this device to Microsoft Apps only.
- The Result: All users accessing the education Institute data for a personal device were required to install the Microsoft Company Portal App to allow management of institute data on their devices and enforce all policies applied to personal devices. This resulted in the institute finding multiple mobile devices that did not have any unlock code and multiple users who were accessing data from non-Microsoft apps that were not manageable via MDM.
5. Session Controls
Conditional Access doesn’t stop working after the initial authentication. It can also control what users can do during their sessions.
How it works: Policies can be set to limit activities like downloading, printing, or copying data from certain applications, even after a user has been granted access.
Why it matters: This can prevent data exfiltration attempts, where a bad actor who has gained access tries to download large amounts of sensitive data.
Real-world example:
- The Problem: An educational institute required that user access to email, Teams chat, and SharePoint documents could not be saved on personal devices.
- The Solution: Conditional Access policies that specifically target any access form a personal device, implementing session controls to block saving on these devices.
- The Result: Users accessing institute data on personal devices was blocked from saving emails, Teams chat and SharePoint documents, users were required to download and install the Microsoft Company Portal app and verify their account. allowing session controls on personal devices and blocking saving data outside of approved Microsoft apps.
Case Study: How our Client Improved Their Security with Conditional Access
Let’s look at how one of our clients, a mid-sized financial services firm, leveraged Conditional Access Policies to enhance their security:
Before implementing these policies, Company X had experienced several minor security incidents, including a case where an employee’s credentials were used to access company data from overseas during a time when the employee wasn’t traveling.
We helped them implement a comprehensive set of Conditional Access Policies, including:
- Geo-location restrictions
- Device management requirements
- Risk-based authentication
The result? In the six months following implementation:
- Suspicious access attempts decreased by 90%
- There were zero successful unauthorised access incidents
- Employee reports of account lockouts due to forgotten passwords decreased, thanks to the more nuanced, risk-based approach
While the IT team initially worried about user pushback, they found that most employees appreciated the additional security, especially once they understood how it protected both the company and their own personal information.
Conclusion
In an era where cyber threats are constantly evolving, static security measures are no longer enough. Conditional Access Policies provide a dynamic, intelligent approach to cybersecurity that can dramatically improve your organisation’s security posture.
By implementing these policies, you can:
- Reduce your risk of data breaches
- Gain greater control over how and where your company resources are accessed
- Adapt your security measures in real-time to respond to potential threats
- Improve overall compliance with data protection regulations
Remember, cybersecurity is not a one-time effort, but an ongoing process. Regularly reviewing and updating your Conditional Access Policies should be a key part of your overall security strategy.
How Grassroots IT Can Help
At Grassroots IT, we specialise in helping businesses leverage the full power of Microsoft 365, including advanced security features like Conditional Access Policies. Our team of experts can:
- Assess your current security posture
- Design and implement Conditional Access Policies tailored to your specific needs
- Provide ongoing support and optimisation of your policies
- Train your team on best practices for cybersecurity
Don’t wait for a security incident to occur. Take proactive steps to protect your organisation today. Contact us for a consultation, and let’s explore how we can enhance your cybersecurity with Conditional Access Policies.