More and more Australian organisations are discovering the strategic advantage of ISO 27001 certification. It’s exciting to see businesses of all sizes embracing this globally recognised security standard, opening doors to new partnerships and market opportunities. What was traditionally the domain of enterprise organisations has evolved into a powerful business enabler for growing companies across the country.
What’s ISO 27001 All About?
Strip away the fancy language, and ISO 27001 is simply an internationally recognised way to prove you’re serious about protecting information. While it might sound complex, at its heart it’s about having a systematic approach to keeping customer data safe, protecting your business from cyber threats, managing access to information, and being prepared when things go wrong. Think of it like a driver’s licence for information security – it proves you know what you’re doing and can be trusted to handle sensitive information properly.
Meeting ISO Requirements with Microsoft 365
The good news is that Microsoft 365 already includes a range of features that can directly support your journey to ISO 27001 compliance. Let’s look at exactly how you can use Microsoft 365 features to meet specific ISO requirements. Here’s your practical guide to ticking those ISO boxes using tools you already have.
User Access Management
What ISO Requires
The standard demands formal processes for managing user access throughout the entire employee lifecycle. This control exists because inappropriate access rights are a major security risk – think ex-employees with active accounts, or staff with more system access than they need. ISO wants to see that you’re actively managing these risks through formal processes and regular reviews. You need a systematic way to grant, modify, and revoke access based on people’s roles, ensuring everyone has exactly what they need to do their job – nothing more, nothing less.
Real-world example
- When Sarah from Accounts leaves, all her access needs to be removed within 24 hours
- When Jim moves from Support to Sales, his system access needs to change to match his new role
- Every quarter, managers need to confirm their team members still need their current access levels
- When Dave from IT needs admin access to fix an urgent issue, it should be time-limited and logged
How to Meet It with Microsoft 365
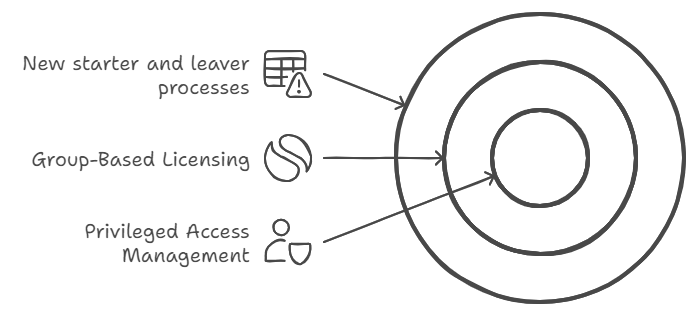
1. For new starter and leaver processes:
- Set up automated workflows in Azure AD: When HR marks an employee as terminated, their accounts are automatically disabled
- Configure group-based licensing: New sales staff automatically get Salesforce access, while marketing gets Adobe Creative Suite
- Use access reviews: Managers get quarterly emails to verify their reports still need access to sensitive data
- Enable Microsoft Groups expiration: Teams/SharePoint access automatically expires if not renewed
2. For privileged access management:
- Set up just-in-time access: IT staff request admin rights for 2 hours to perform maintenance
- Configure approval workflows: Senior IT approval required for global admin access
- Enable session recording: All admin activities in sensitive systems are logged
Authentication Controls
What ISO Requires
You need to prove you’re properly controlling system access. This requirement recognises that passwords alone aren’t enough anymore. ISO wants evidence that you’re using modern authentication methods to verify users’ identities, especially when accessing sensitive information or systems. It’s about making sure that even if someone gets hold of a password, they can’t automatically access your systems. The standard also emphasises the importance of protecting access information – like making sure password rules are strong enough and that you can detect and block suspicious login attempts.
Real-world examples:
- Jane shouldn’t be able to log in with just a password when accessing payroll data from home
- Failed password attempts should lock an account after 5 tries
- If Bob’s session is idle for 15 minutes, he should be logged out
- When Alice tries to log in from an unusual location, extra verification should be required
How to Meet It with Microsoft 365
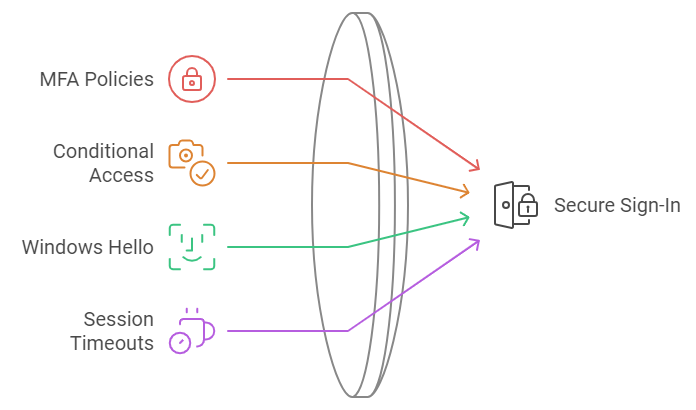
1. For secure sign-in:
- Configure MFA policies: Force additional verification for all remote access
- Set up Conditional Access: Require managed devices for accessing customer data
- Enable Windows Hello: Replace passwords with biometric login
- Configure session timeouts: Auto-logout after 15 minutes of inactivity
Information Classification
What ISO Requires
You must show that sensitive information is properly identified and protected. This control recognises that not all information needs the same level of protection – your marketing brochure doesn’t need the same security as your customer credit card details. ISO requires you to think through what types of information you handle, how sensitive each type is, and what protection it needs. Then you need to show that you’ve got systems in place to consistently identify and protect information based on its sensitivity level.
Real-world examples:
- Customer credit card details need the highest level of protection
- Internal project documents shouldn’t be shareable outside the company
- HR documents should only be accessible by the HR team
- Marketing materials can be widely shared but not modified by everyone
How to Meet It with Microsoft 365
1. For automatic classification:
- Create sensitivity labels: “Confidential-Finance”, “Internal-Only”, “Public”
- Configure auto-labelling: Documents with credit card numbers automatically marked as “Confidential”
- Set up visual markers: Confidential documents get a red header saying “Internal Use Only”
2. For information handling:
- Enable encryption: “Confidential” documents can only be opened by approved users
- Set up DLP: Block sharing of documents containing tax file numbers
- Configure SharePoint permissions: HR site only accessible by HR team members
Cryptographic Controls
What ISO Requires
Sensitive data must be properly encrypted. This requirement goes beyond just turning on encryption – ISO wants to see that you’ve thought through when and where encryption is needed, and that you’re managing it properly. This includes having formal policies about what needs to be encrypted, managing encryption keys securely, and making sure your encryption methods are strong enough for the sensitivity of the data you’re protecting. It’s about ensuring that if someone does get unauthorized access to your systems, they still can’t read your sensitive data.
Real-world examples:
- Client contracts must be encrypted when stored
- Financial reports being emailed to the board need encryption
- Mobile devices with company data must be encrypted
- Backup files need to be encrypted before going to cloud storage
How to Meet It with Microsoft 365
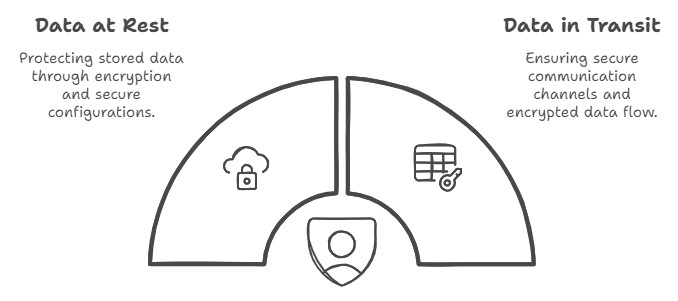
1. For data at rest:
- Enable BitLocker: All laptop drives automatically encrypted
- Configure SharePoint encryption: All documents encrypted with unique keys
- Set up Exchange mailbox encryption: Emails encrypted by default
2. For data in transit:
- Enable TLS: All email communications encrypted in transit
- Configure secure external sharing: Client portal access using encrypted connections
- Set up encrypted backup: Automatic encryption before cloud backup
Logging and Monitoring
What ISO Requires
ISO needs you to prove you’re actively monitoring your systems. This means having systems in place to detect, capture, and investigate security events and user activity. It’s not just about recording what happens – you need to show that you’re actively reviewing these records and can spot potential security incidents quickly. Think of it like CCTV for your IT systems – it needs to be recording, but someone also needs to be watching the monitors.
Real-world examples:
- All admin actions in key systems need to be logged and reviewable
- Failed login attempts need to be monitored and investigated
- File access patterns need to be tracked to spot unusual behaviour
- System changes need to be logged and attributable to specific users
How to Meet It with Microsoft 365
1. For audit logging:
- Enable Unified Audit Logging in Security & Compliance
- Configure alert policies for sensitive actions
- Set up log retention policies for compliance
2. For security monitoring:
- Enable Microsoft Defender for Cloud Apps
- Configure alert policies for suspicious activities
- Set up automated incident reporting
Communications Security
What ISO Requires
Information needs to be protected whenever it’s being shared or moved around. This control focuses on keeping data safe when it’s in transit between systems or being shared with external parties. It’s about making sure sensitive information can’t be intercepted or tampered with when it’s moving between point A and point B, whether that’s within your network or out to external partners.
Real-world examples:
- Customer data being shared with partners needs encryption
- Confidential emails need to be protected from interception
- File transfers between systems need to be secure
- External collaboration needs to be controlled and monitored
How to Meet It with Microsoft 365
1. For email security:
- Enable Exchange Online Protection
- Configure anti-phishing policies
- Set up Safe Attachments and Safe Links
2. For secure file sharing:
- Configure SharePoint sharing policies
- Enable Teams external access controls
- Set up secure guest access policies
The Bottom Line
Getting ISO 27001 certified doesn’t mean buying new security tools. Microsoft 365 includes powerful features that map directly to ISO requirements – you just need to know what to turn on and how to configure it.
Need help setting up these controls or mapping them to your ISO requirements? That’s what we do. Let’s talk about getting your Microsoft 365 environment ISO-ready.